
Shared Account Password Management: Secure & Easy Solutions
Share
The Hidden Risks of Shared Passwords

Sharing passwords seems convenient, but it exposes organizations to serious security vulnerabilities. This practice weakens even the most robust password policies, creating easy entry points for attackers. Let's explore the dangers of this common, yet risky behavior.
The Impact on Security
One major risk of shared passwords is the loss of accountability. When many people access an account with the same credentials, tracking individual actions becomes impossible. This makes it difficult to identify the source of errors, breaches, or malicious activity. The resulting lack of traceability can have severe legal and financial consequences.
Additionally, shared passwords dramatically increase the risk of unauthorized access. If one person’s device is compromised, the entire account is vulnerable. This can lead to data breaches, financial losses, and damage to your reputation. A compromised social media account, for example, could be used to spread misinformation or launch phishing attacks. The common practice of password reuse further amplifies this risk.
Furthermore, shared passwords often lead to weaker password hygiene. People are less likely to create strong, unique passwords if they're meant to be shared. This creates an exploitable vulnerability for hackers. Many individuals simply don't follow password best practices. Despite the risks, approximately 17% of users admit to sharing social media and online shopping passwords in 2025. Coupled with the fact that 75% of people globally don't follow accepted password best practices, this creates a significant security gap. Even in IT, 53% of professionals admit to sharing passwords. For more statistics, check out this resource: Password Statistics.
Operational Inefficiencies
Shared passwords also create operational inefficiencies. Managing access becomes cumbersome, especially when employees leave. Revoking access often requires changing the password, disrupting everyone else using that account.
Password sharing also hinders incident response. During a security incident, quickly identifying and isolating affected accounts is critical. Shared credentials make this process much slower and more complex, potentially escalating the breach and magnifying the damage.
Building a Culture of Security
Creating a security-first password culture requires a multi-faceted approach, combining technology and education. Resources on creating a culture of security can offer valuable guidance for organizations. Robust shared account password management solutions, like AccountShare, enhance security without sacrificing convenience. (This link is a placeholder, as "AccountShare" does not appear to be an established product.) By centrally controlling shared credentials, these platforms mitigate the risks of traditional password sharing and streamline workflows. These tools are essential for transitioning from risky practices to a more secure and productive digital environment.
The Password Burden: Understanding the Scale of the 2025 Challenge
The sheer volume of online accounts needed for both personal and professional life has created a major problem: password fatigue. This isn't just a minor annoyance; it's a serious security risk. Teams manage dozens of shared accounts across multiple platforms, creating a significant cognitive burden. This constant struggle to remember credentials often leads even security-conscious teams to take risky shortcuts.
The Cognitive Overload of Shared Accounts
Imagine trying to remember the combination to dozens of locks, each subtly different. This is the reality for many professionals managing shared account passwords. The mental effort spent tracking these credentials takes away from focused work, impacting overall productivity. Constantly resetting forgotten passwords or dealing with complicated login procedures disrupts workflows and wastes precious time.
The issue is further complicated by differing security requirements for each platform. Some require complex passwords with special characters, while others enforce stricter password expiration policies. This inconsistency contributes to cognitive overload and increases the chance of human error.
The Dangerous Shortcuts and Their Consequences
Overwhelmed by the number of passwords they need to manage, teams often resort to insecure practices. These shortcuts might offer temporary relief, but they introduce significant security vulnerabilities. Some common examples include:
- Using weak, easy-to-guess passwords: This leaves accounts vulnerable to attackers.
- Reusing the same password on multiple platforms: If one account is compromised, every account using that same password is at risk.
- Storing passwords insecurely: Writing passwords down or sharing them through email or chat exposes them to unauthorized access.
- Disabling multi-factor authentication (MFA): While MFA adds an extra security layer, its added steps can be cumbersome. Disabling it for convenience weakens overall security.
These risky practices can result in data breaches, financial loss, and damage to an organization's reputation. The impact goes beyond the individual user, affecting the entire organization. A 2025 global study reveals the extent of this problem: individuals manage an average of 70 to 80 passwords, with over 417 billion accounts worldwide requiring password management. Professionals log in 10 to 15 times every day, increasing the strain. Find more detailed statistics here.
Varying Challenges Across Different Organizations
The challenges of shared account password management differ based on an organization's size and industry. Smaller businesses might lack resources for dedicated IT support, leaving individual employees responsible for managing shared accounts. Larger organizations may face complex access control issues because of the number of users and departments involved.
Highly regulated industries, such as healthcare and finance, face the added pressure of complying with strict security standards. This adds another layer of complexity to their password management strategies. Understanding these unique challenges is key to creating effective and practical solutions. These solutions must find a balance between strong security and ease of use to ensure organization-wide adoption and effectively mitigate the risks associated with shared credentials.
Building a Fortress: Best Practices for Shared Credentials
Shared account password management is more than just a technical challenge; it’s a delicate balance between security and productivity. Finding this equilibrium is critical for protecting sensitive data while ensuring smooth collaboration. This section explores proven strategies for building a reliable system to manage shared credentials.
Defining Shared Access Needs
The first step toward secure shared account password management is identifying which accounts truly require shared access. Not every account needs multiple users. Begin by auditing all shared accounts. Categorize them by sensitivity and intended use. For example, access needs for a social media account will differ from those of a financial system login. You might find this interesting: How to master secure password sharing.
Crafting Strong Password Policies for Shared Accounts
After identifying which accounts require shared access, create clear and enforceable password policies. These should be stricter than those for individual accounts. Consider these best practices:
- Strong Passwords: Mandate complex passwords with a mix of uppercase and lowercase letters, numbers, and symbols. Password length should align with industry standards.
- Regular Rotation: Rotate shared passwords often—ideally every 30-90 days. This minimizes damage if credentials are compromised.
- Limited Access: Grant the minimum necessary access to each user. Avoid granting administrative privileges to everyone unless absolutely required.
Implementing Access Governance
Effective access governance is the foundation of secure shared account password management. Implement a system that regulates who can access which accounts and their permitted actions. This might involve using a Privileged Access Management (PAM) system like CyberArk or a dedicated password manager such as LastPass for shared accounts.
Regularly review and update access permissions, especially when employees join or leave the company. This prevents former employees from accessing sensitive data.
Secure Onboarding and Offboarding
Establish robust onboarding and offboarding processes specifically for shared accounts. During onboarding, clearly explain password policies and provide training on secure access. During offboarding, instantly revoke access to all shared accounts to prevent credential leakage.
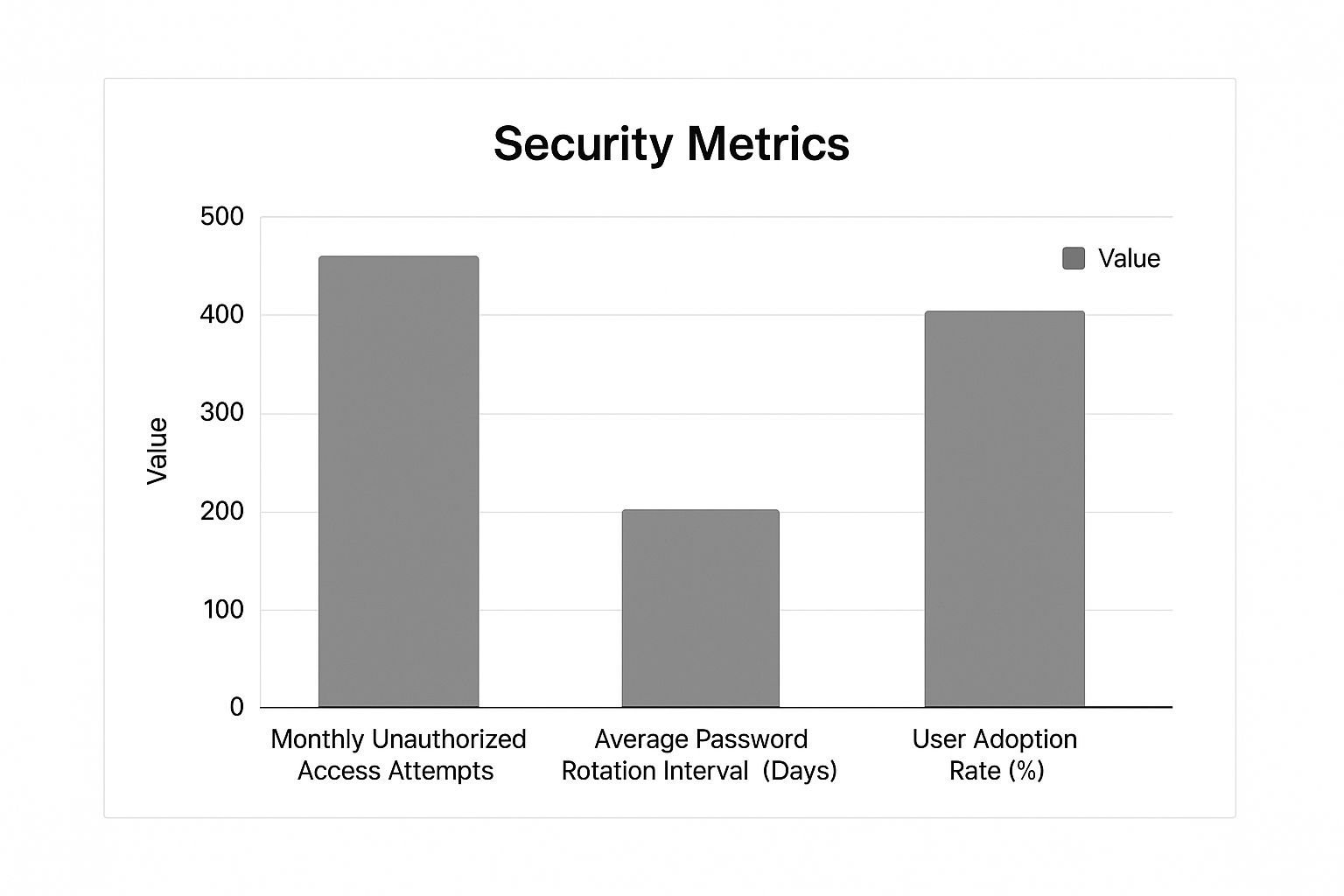
The infographic above visualizes key metrics related to shared account password management. These metrics include monthly unauthorized access attempts, average password rotation interval, and user adoption rate. The data demonstrates that robust password policies and frequent rotations significantly decrease unauthorized access, all while maintaining high user adoption. This proves security and usability can go hand in hand.
To further understand the different strategies for managing shared passwords and their security implications, the following table offers a helpful comparison:
Shared Password Security Best Practices Comparison This table compares various approaches to shared password management, highlighting their security benefits and operational factors.
| Management Approach | Security Level | Ease of Implementation | User Experience | Audit Capabilities | Best For |
|---|---|---|---|---|---|
| Plain Text Sharing | Very Low | Very Easy | Simple but Risky | None | Absolutely Avoid |
| Shared Spreadsheet/Document | Low | Easy | Inconvenient | Limited | Small Teams, Low Risk Tolerance |
| Password Manager (Consumer Grade) | Medium | Moderate | Convenient | Basic | Small to Medium Teams |
| Privileged Access Management (PAM) | High | Complex | Secure, Streamlined | Comprehensive | Large Enterprises, High Security Needs |
| Dedicated Shared Account Password Manager | High | Moderate | User-Friendly, Secure | Detailed | Medium to Large Teams, Enhanced Security |
This comparison reveals that while simple methods like plain text or spreadsheets offer convenience, they lack vital security features. More advanced solutions such as PAM and dedicated password managers provide stronger security, detailed audit trails, and a better user experience, albeit with increased complexity.
Adapting to Different Operational Requirements
One size doesn't fit all. Organizations must tailor these best practices to their individual requirements. Smaller businesses might find basic solutions adequate, while larger enterprises require more sophisticated systems. Learn more in our article about shared password management for teams. Regardless of size, the core principles remain constant: strong passwords, regular rotation, controlled access, and effective onboarding/offboarding processes. Implementing these strategies strengthens any organization's security posture against the risks associated with shared credentials.
Selecting The Right Password Management Arsenal

Choosing the right tools for shared account password management can be a daunting task. With a plethora of options on the market, separating effective solutions from marketing hype requires careful consideration. You need to thoroughly evaluate features, security, and how well the tool integrates with your existing systems. For a deeper dive into password management tools, check out our guide on the best password management tools.
Evaluating Enterprise Password Managers
Enterprise Password Managers (EPMs) offer a centralized platform for storing and managing shared credentials. These solutions typically include features like access controls, password generators, and automatic password rotation.
However, it's essential to understand that not all EPMs are built the same. Some may lack crucial features necessary for effectively managing shared accounts, such as granular permission settings and detailed audit logs. This can leave security gaps.
For instance, some EPMs allow password sharing but don't offer control over how each user utilizes those credentials. This can be a significant security risk. Furthermore, incomplete audit logs hinder the ability to track account activity and identify potentially suspicious behavior.
Privileged Access Management (PAM) Systems
Privileged Access Management (PAM) systems provide a more robust approach, prioritizing the security of highly sensitive accounts with elevated privileges. These systems often incorporate features like session recording, multi-factor authentication (MFA) enforcement, and just-in-time access. This ensures that only authorized personnel can access critical systems.
PAM is particularly valuable for shared account password management involving high-value accounts, such as domain administrator credentials. However, the complexity and cost associated with PAM systems can make them less suitable for smaller organizations or teams with less demanding security requirements.
Exploring Specialized Vaulting Solutions
Specialized vaulting solutions focus on securing sensitive data such as API keys, database credentials, and other confidential information. These solutions generally come with robust encryption and access control features.
They are designed for teams that need to share sensitive information securely without needing the full functionality of a PAM system. This makes them a compelling middle ground for organizations seeking greater security than a basic EPM but without the intricacies of a full-blown PAM solution. Successful implementation, however, relies heavily on smooth integration with existing workflows.
Key Features To Consider For Shared Accounts
Effective shared account password management hinges on several key features. These features directly impact both security and ease of use.
When comparing different tools, keep an eye out for the following:
- Granular Access Controls: The ability to assign specific permissions for each user is critical.
- Detailed Audit Logs: Comprehensive records of all account activity are essential for monitoring and security.
- Automated Password Rotation: Regularly changing passwords automatically enhances security without manual intervention.
- Integration with Existing Systems: Seamless compatibility with your current tools and workflows streamlines operations.
- MFA Support: Implementing strong authentication for all shared accounts is non-negotiable.
To help illustrate the differences between these solutions, let's look at a comparison of some leading enterprise password management solutions:
Enterprise Password Management Solutions Comparison
| Solution | Shared Account Features | Access Controls | Compliance Support | Price Range | Ideal Organization Size |
|---|---|---|---|---|---|
| Example Solution 1 | Granular Permissions | Role-Based Access | SOC 2, ISO 27001 | $5-$10 per user | Small to Medium |
| Example Solution 2 | Shared Vaults | Group-Based Access | HIPAA, GDPR | $10-$20 per user | Medium to Large |
| Example Solution 3 | Session Recording | Attribute-Based Access | PCI DSS | $20-$30 per user | Large Enterprises |
This table highlights the varying strengths of different solutions. Choosing the right solution depends on your specific needs and budget.
Password management insecurity remains a persistent global issue. In 2025, over 64% of internet users reported low confidence in their password management, with only 12% consistently using unique passwords. Find more detailed statistics here. This underscores the need for user-friendly solutions that promote secure practices. Ultimately, selecting the right password management solution requires careful consideration of your organization's unique needs, size, and current infrastructure to find the optimal balance between security and usability.
From Theory to Practice: Implementing Your Password Strategy
Implementing a robust shared account password management strategy takes more than just understanding the basics. You need a practical plan to put these concepts into action. This section offers a roadmap, based on insights from organizations that have successfully strengthened their password practices. For a deeper dive into this topic, check out this helpful resource: How to master shared password management for your team.
Conducting a Comprehensive Credential Audit
The first step is to assess your current state. Conduct a full audit of all shared credentials across your organization. This means identifying:
- Which accounts are shared: Compile a list of every account accessed by multiple users.
- Who has access to each account: Keep a record of each individual with access privileges.
- The level of access granted: Specify whether users have administrative, editing, or viewing permissions.
- How passwords are currently managed: Determine how passwords are being stored – are they in plain text, spreadsheets, or a dedicated password manager?
This audit will reveal your organization's actual risk exposure, highlighting vulnerabilities and pinpointing areas needing immediate action.
Prioritizing Critical Shared Accounts
Not all accounts are created equal. Prioritize those that grant access to sensitive data, such as financial systems, customer databases, or intellectual property. These high-value accounts require the strongest protection and should be addressed first. For a robust solution, consider platforms like Tevello which offer a wide range of features for managing shared accounts.
For instance, shared administrative accounts often have extensive access, making them attractive targets. Implement strong security measures like multi-factor authentication (MFA) and regular password rotations to minimize risk.
Developing Practical Password Policies
Effective password policies are essential. These policies must be actionable and relevant to collaborative work.
Here are a few best practices:
- Strong, Unique Passwords: Mandate complex passwords unique to each shared account.
- Regular Password Rotations: Establish a regular rotation schedule. Every 90 days is a good starting point, but adjust based on the account's sensitivity.
- Principle of Least Privilege: Grant only the minimum access required for each user. Avoid giving administrative privileges unless absolutely necessary.
Phased Implementation and Team Adoption
Implementing a new password strategy can disrupt established workflows. A phased rollout minimizes disruption and encourages buy-in. Begin by focusing on the most critical accounts, then gradually extend to other areas.
Offer thorough training and support to your team. Explain why the changes are important and how they benefit security. Address concerns and highlight the advantages of a more secure system.
Establishing Meaningful Success Metrics
Tracking progress is key for sustained success. Define clear metrics to gauge the effectiveness of your password management strategy. These metrics should go beyond basic compliance checklists.
Focus on metrics such as:
- Reduction in unauthorized access attempts: This indicates increased security.
- Improved password hygiene: Monitor the strength and uniqueness of shared passwords.
- Time saved through streamlined workflows: Showcase the productivity gains of a well-implemented system.
By following these steps, organizations can move from theory to practice, building a robust shared account password management strategy that enhances security without sacrificing efficiency. This proactive approach significantly reduces the risks tied to shared credentials, fostering a security-conscious culture.
Building a Security-First Password Culture

Implementing the right technology for shared account password management is only half the battle. The other half hinges on fostering a strong security culture within your team. This involves not just implementing new tools, but changing behaviors and attitudes towards password security. This crucial shift requires a proactive and ongoing effort.
Targeted Education Initiatives for Behavior Change
Simply telling people to use strong passwords isn't enough. Effective training programs go beyond simple policy awareness. They focus on practical skills and real-world scenarios.
For example, simulated phishing attacks can illustrate how social engineering tactics work and how to identify them. This interactive approach reinforces learning and makes security training more engaging.
Additionally, tailor training content to different roles within the organization. Executives need to understand the business risks of poor password practices, while technical staff needs in-depth knowledge of the chosen password management solution. Occasional system users benefit from simplified training focused on essential security principles.
Creating Compelling Security Narratives
Effective security awareness programs often use compelling narratives to connect with employees on a personal level. Stories about data breaches or security incidents can highlight the real-world consequences of weak passwords.
However, it’s important to also focus on the positive impact of strong security practices. For instance, explain how secure password sharing can protect both the company and employees’ personal data. Frame security as a shared responsibility that benefits everyone.
Embedding Secure Practices into Everyday Workflows
True cultural change requires integrating secure password practices into daily routines. This means making secure behaviors the easiest and most intuitive option.
For example, integrate the chosen password management solution directly into common work applications. This reduces friction and encourages consistent use.
Furthermore, promote the use of password generators to create strong, unique passwords for every shared account. Integrate these generators directly into the password manager to simplify the process and eliminate the temptation to use weak, easily guessed passwords.
Countering Social Engineering and Establishing Emergency Procedures
Security training must address social engineering tactics, which attackers frequently use to obtain passwords. Teach your team how to recognize suspicious emails, phishing attempts, and other manipulative tactics. Encourage healthy skepticism and empower them to report anything unusual.
Additionally, establish clear emergency procedures for security incidents. Outline the steps to take if a shared account is compromised, who to contact, and how to contain the breach. This rapid response plan can minimize the damage caused by a security incident.
Ready to Elevate Your Team’s Security?
By building a security-first culture, you transform your team into your strongest defense against cyber threats. This cultural shift complements your technical solutions, creating a robust and resilient security posture.
Start streamlining your shared accounts and building a more secure collaborative environment with AccountShare today. Visit AccountShare now to discover how easy and affordable secure password management can be.
