
Team Password Sharing: Secure Your Modern Team's Data
Share
The Hidden Reality of Team Password Sharing
Team password sharing. It's a common practice in collaborative work environments. But beneath this seemingly harmless habit lies a serious security risk that many teams underestimate. This isn't about blaming individuals, but rather understanding the human factors that lead even security-conscious teams to engage in risky password behaviors.
One of the main drivers is the constant pressure to be efficient. Tight deadlines and urgent projects create an environment where quick access to tools is paramount. Secure password management can feel like a hindrance to productivity in these high-pressure situations. This often leads to shortcuts, like emailing passwords or writing them down in shared documents. These actions, while convenient in the moment, create significant vulnerabilities.
This isn't a rare occurrence. A study found that 53% of IT professionals, the very people responsible for data security, admitted to sharing passwords via email. Other methods include sharing passwords through online documents (43%) and messaging apps (41%). This reveals a gap between security awareness and actual practice. For more detailed statistics, check out this resource: Learn more about password sharing statistics.
The Psychology of Password Sharing
The psychology behind password sharing is rooted in convenience and a sense of trust within the team. Sharing a password can seem like a simple act of collaboration, much like lending a colleague a pen. However, this analogy misses a critical difference: a compromised password unlocks access to sensitive data, potentially exposing the entire organization to a security breach.
The Danger of Shared Accounts
The problem is amplified by the use of shared accounts. Imagine multiple team members using the same login for a crucial platform. If a security incident occurs, tracing the source becomes incredibly difficult. Accountability disappears, and valuable time is wasted trying to pinpoint the responsible individual. This lack of transparency hinders incident response and can worsen the damage from an attack. It highlights the need for a more secure and accountable system for managing access, a topic we'll explore further.
When Convenience Becomes Catastrophic: The Real Risks
Sharing passwords might seem like a harmless shortcut, but it creates serious security risks for your organization, often with devastating consequences. These risks are frequently overlooked until a security breach occurs, forcing a painful and expensive reckoning. Let’s explore how seemingly small acts of convenience can escalate into major security incidents.
One significant risk is password sprawl. As passwords are shared and reused across multiple platforms and among team members, it creates a complex web of access points. This makes tracking who has access to what nearly impossible.
For example, imagine a former employee still having access to sensitive data months after leaving the company simply because their shared credentials were never revoked. This expanding security debt compounds over time, creating vulnerabilities ripe for exploitation.
Additionally, team password sharing undermines accountability. If everyone uses the same login, how can you identify who made a specific change or inadvertently caused a security incident? This lack of clarity creates blind spots during investigations, hindering your ability to learn from mistakes and prevent future breaches.
This ambiguity can also foster distrust and finger-pointing within the team. You might be interested in: How to master....
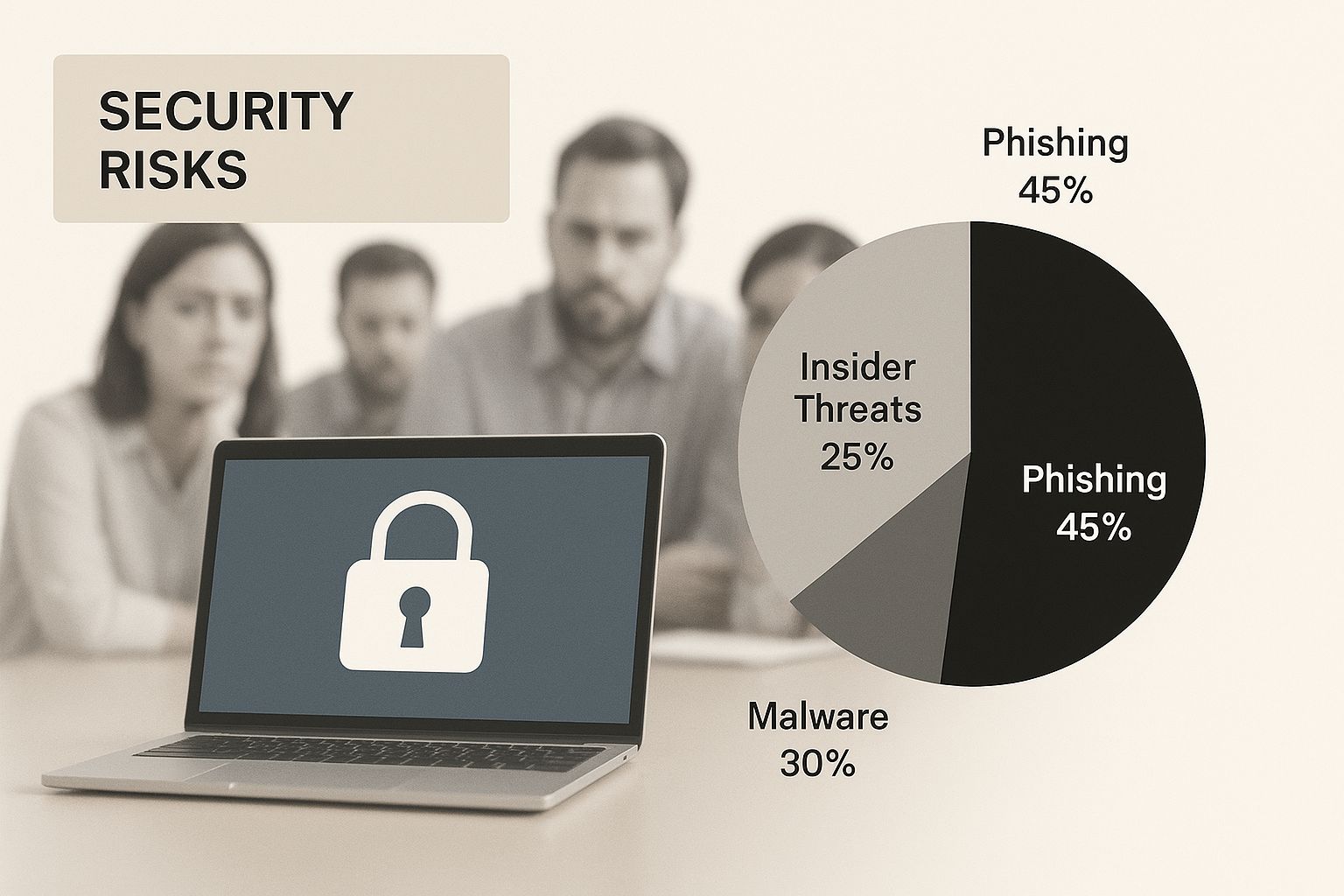 This infographic visualizes the security risks associated with team password sharing, depicting a digital padlock on a laptop with concerned team members in the background.
This infographic visualizes the security risks associated with team password sharing, depicting a digital padlock on a laptop with concerned team members in the background.
The image highlights the inherent tension between perceived convenience and the very real dangers of compromised security. This visual emphasizes the critical need to address password sharing practices before a breach occurs.
Compliance Implications and Regulatory Penalties
Password sharing also carries significant compliance implications, especially for regulated industries. Failing to comply with industry standards for credential management can lead to hefty fines and legal repercussions. These penalties extend beyond the immediate costs of a breach, adding long-term financial strain and damaging your reputation.
The Broader Problem of Password Management
The tendency toward risky password sharing often originates from broader password management issues. Research shows that 47% of people have shared personal passwords, often without additional security measures. In professional settings, 37% admit to using the same password for multiple accounts.
The average employee reuses a password approximately 16 times. This widespread reuse and sharing significantly increases vulnerability to cyber threats. Find more detailed statistics here: The Biggest Password Trends.
To further illustrate the risks associated with different sharing methods, let's examine the following comparison:
Common Password Sharing Methods & Security Risks
| Sharing Method | Usage Percentage | Convenience Level | Security Risk Level | Potential Vulnerabilities |
|---|---|---|---|---|
| Shared Spreadsheet/Document | High | High | Very High | Unauthorized access, data breaches, difficult to track changes |
| Plain Text Email/Messaging | Very High | High | Extremely High | Interception, phishing, lack of access control |
| Password Manager (Unshared) | Low | Medium | Low | Device compromise, master password vulnerability (if weak) |
| Password Manager (Shared) | Medium | High | Medium | Dependent on password manager's security features, potential insider threats |
| Dedicated Access Management System | Low | Medium | Very Low | Strongest security, centralized control, audit trails |
This table demonstrates how convenient methods often carry the highest security risks. While shared spreadsheets or plain text communication might seem easy, they are extremely vulnerable to unauthorized access and data breaches. Using a dedicated access management system, while potentially less convenient, provides the strongest security posture.
This confluence of convenience, human behavior, and technical vulnerabilities emphasizes the urgent need for more secure password management solutions. Prioritizing both security and efficient workflows is paramount.
Modern Solutions That Actually Work

Modern password management solutions offer secure and efficient ways for teams to share credentials.
Sharing team passwords insecurely poses significant risks. Addressing these risks requires solutions built for today's complex work environments. Thankfully, robust password management platforms offer practical ways to boost security without impacting your team's efficiency. These platforms offer a range of features specifically designed for secure and efficient team password sharing. This allows teams to collaborate effectively while maintaining strong security practices.
Key Features of Effective Solutions
Effective team password sharing solutions do more than just store passwords. They include features that target the root causes of insecure practices.
-
Role-Based Access Controls: Team members only access the credentials they absolutely need. This principle of least privilege limits the damage from a single compromised account.
-
Emergency Access Provisions: Business continuity is assured, even if a key team member is unavailable. Imagine needing urgent access to a critical system, but the password holder is out of reach. Emergency access procedures handle these situations, keeping operations running smoothly during crises.
-
Comprehensive Audit Logging: This vital feature tracks who accessed what and when. This provides valuable information during security incidents. Audit trails create accountability and allow for faster, more effective incident response.
Cloud-Based vs. Self-Hosted: Choosing the Right Deployment
Two common deployment methods exist for team password sharing solutions: cloud-based and self-hosted. Cloud-based solutions offer easy accessibility and implementation. However, convenience may involve security trade-offs depending on the provider's infrastructure and security protocols.
Self-hosted solutions give organizations more control over their data and security. This control comes with increased implementation and maintenance responsibilities. The best deployment method depends on your team structure, security needs, and IT resources.
Finding the Perfect Fit: Real-World Examples
Consider a marketing team needing access to social media and analytics dashboards. A cloud-based password manager like LastPass with role-based access controls would be a good fit. This lets different team members access appropriate credentials based on their roles.
For a software development team working with sensitive source code, a self-hosted solution like Bitwarden with robust security protocols may be better. This offers tighter access control and protects valuable intellectual property.
To help you choose the right solution, let's look at a comparison of some popular options:
The following table compares several top password management solutions designed for secure team password sharing.
Team Password Management Solutions Comparison
| Solution | Key Features | Security Protocols | Price Range | Best For | Limitations |
|---|---|---|---|---|---|
| LastPass | Role-based access, 2FA, audit logs | AES-256 encryption | $3 - $6/user/month | Small to medium teams | Limited integrations with some enterprise tools |
| Bitwarden | Self-hosted, granular permissions, version control | Customizable encryption | Open Source (free), paid plans from $10/year | Large teams, high-security needs | Requires IT management for self-hosting |
| 1Password | Mobile access, password generator, sharing options | End-to-end encryption | $2.99 - $7.99/user/month | Individuals and small teams | Fewer advanced features compared to enterprise solutions |
This table highlights the different features, security protocols, and pricing of team password management solutions. This variety helps you select a solution aligned with your organization's needs and budget. Adopting these modern solutions significantly improves your security while keeping the collaborative workflows essential for success. Choosing the right solution balances security and efficient workflows for your team.
Building Your Password Sharing Playbook

Visual representation of a team collaborating on a secure password management strategy.
This section offers a practical roadmap for implementing and managing shared credentials, going beyond just selecting the right password management solution. This approach will improve how your team handles passwords, focusing on both security and efficiency.
Establishing the Principle of Least Privilege
A successful team password sharing strategy begins with the principle of least privilege. This core concept means giving each team member access only to the passwords they absolutely need for their job. For instance, a marketing intern shouldn't have access to the company's sensitive financial data.
This targeted approach limits the damage from potential security breaches. By containing the impact of any compromised account, you're strengthening your overall security. Careful planning and a clear understanding of each person's responsibilities are key. Defining access levels improves security and makes it easier to track activity. You might be interested in: Learn more in our article about...
Developing Password Rotation Schedules
Password rotation is essential for security. However, frequent rotations can be disruptive if not done carefully. The goal is to balance security with practicality. A common starting point is rotating passwords every 90 days.
However, consider the sensitivity of the accessed information. More sensitive data requires more frequent changes. Adjust your rotation schedule accordingly to ensure the highest level of protection for critical systems.
Creating Emergency Access Protocols
Unforeseen circumstances happen. What if a key team member is suddenly unavailable, but their access is urgently needed? Emergency access protocols are vital for business continuity. These protocols outline how designated individuals can access critical systems in emergencies.
This might involve a manager accessing a secure vault with emergency credentials, combined with strict logging procedures. Thinking ahead and having a plan prevents disruptions and maintains productivity during critical moments.
Overcoming Resistance to Change
Introducing new security measures can sometimes meet with resistance. Team members might see password management solutions as extra work. Addressing these concerns head-on is crucial for successful adoption. For smaller teams, individual conversations explaining the benefits can be very effective.
Larger organizations may need more formal training and clear communication about the reasons behind the changes. Highlighting the positives, like reduced breach risk and improved accountability, encourages acceptance.
Measuring Compliance and Maintaining Momentum
After setting up your password sharing system, ongoing monitoring is key. Regularly review access logs and perform periodic audits. This confirms the system is being used properly and the principle of least privilege is being followed. These checks also help identify any weaknesses in your security practices.
For instance, you can track how often passwords are rotated and monitor adherence to emergency access protocols. These metrics maintain a strong security posture and help you address any vulnerabilities that arise. This continued commitment to security helps your team stay protected.
Transforming Your Team's Security Mindset
Even the most advanced security tools are useless without team buy-in. This section explores why traditional security training often falls short and how forward-thinking organizations are improving their approach to team password sharing. Through real-world examples of successful security transformations, you'll discover how to create engaging training that connects security practices to personal values, rather than just abstract rules.
Engaging Your Team Through Values-Based Training
Traditional security training often centers on policies and procedures, which can feel disconnected from employees' day-to-day tasks. This approach can create a gap between what people know they should do and what they actually do.
Instead, try linking security practices to personal values. For example, highlight how strong passwords protect not only company data but also an individual's personal information. This makes security more relatable and encourages responsible behavior.
Microlearning and Attention Spans
Today's learners often have limited attention spans. Microlearning, delivering training in short, focused bursts, can be significantly more effective than long lectures. Think short videos, interactive quizzes, or quick tips delivered via email.
This approach makes learning easier to absorb and incorporate into busy schedules. You might be interested in: Learn more in our article about...
Gamification and Storytelling: Making Security Memorable
Gamifying security training can boost engagement and knowledge retention. Consider awarding points for completing training modules or setting up friendly competitions between teams.
Storytelling can also make security concepts more accessible and memorable. Share real-world examples of breaches resulting from poor password sharing or create scenarios that illustrate the positive impact of good security practices.
The Power of Peer Influence
Team members frequently turn to one another for guidance. Identify security champions within your team to model good security behaviors and motivate others.
These individuals can be invaluable assets for their colleagues, addressing questions and offering support as the team transitions to more secure practices. This peer-to-peer method can be far more effective than top-down directives.
Reinforcement and Avoiding Security Fatigue
Consistent reinforcement is crucial for lasting behavior change. Regularly remind team members about best practices for team password sharing.
However, avoid overwhelming them with continuous alerts and warnings, which can cause security fatigue. Strive for a balance that keeps security a priority without causing undue stress. This could involve distributing monthly newsletters with security tips or holding brief refreshers during team meetings. The goal is to cultivate a culture of security that feels integrated into daily workflows.
Beyond Passwords: Next-Generation Team Authentication
Team password sharing is a common practice, but it comes with significant security risks. The future of team security lies in moving beyond passwords entirely. This section explores practical authentication alternatives that forward-thinking organizations are already adopting. We'll examine real-world applications of multi-factor authentication, biometric verification, single sign-on, and true passwordless authentication within team environments.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) adds layers of security beyond a simple password. It requires users to provide multiple verification factors. These factors often fall into categories like something they know (a password), something they have (a security token), or something they are (biometric data). This approach makes unauthorized access significantly harder, even if a password is compromised.
For example, a team member might enter their password and then receive a verification code on their phone. They must then enter this code to gain access. This additional step creates an important security barrier.
Biometric Verification
Biometric verification uses unique physical characteristics to confirm a user's identity. These characteristics can include fingerprints or facial recognition. Biometrics offer strong security because these traits are difficult to replicate.
However, implementing biometric verification can be more complex and expensive than other methods. It also raises important privacy concerns that organizations must address carefully.
Single Sign-On (SSO)
Single sign-on (SSO) allows users to access multiple applications with a single set of credentials. This simplifies the login process and improves security by reducing the number of passwords users need to remember. This, in turn, reduces the risk of passwords being compromised or misused.
To enhance security further, consider integrating with identity management systems like Okta. LeaveWizard's Okta integration is a good example of how this can work. SSO streamlines access for teams while maintaining strong security.
True Passwordless Authentication
Passwordless authentication eliminates passwords altogether. This approach often uses methods like magic links sent to a user's email or device-based authentication. While this offers the highest level of security against password-based attacks, the user experience can be a key consideration during implementation.
Ensuring a smooth transition for your team requires careful planning and effective training. Clear communication and support will be crucial for successful adoption.
Migration Strategies and Practical Considerations
Moving away from team password sharing requires a well-defined strategy. Here are some key considerations:
-
Realistic Timelines: Don't expect an overnight change. Phased rollouts allow teams to adapt to new authentication methods gradually.
-
Change Management: Clearly communicate the benefits of the new authentication methods to your team and address any concerns. This will help ensure a smooth transition.
-
Success Metrics: Track key metrics, such as the number of MFA enrollments or a reduction in password-related support tickets, to measure the effectiveness of the new authentication methods.
| Authentication Method | Security Benefits | Implementation Challenges | User Experience Impact |
|---|---|---|---|
| MFA | Significantly reduces risk of unauthorized access | Requires user training and setup | Adds extra steps to the login process |
| Biometrics | Strong security based on unique physical traits | Can be complex and expensive to implement; privacy concerns | Can be convenient and secure once set up |
| SSO | Simplifies access and reduces number of passwords | Requires integration with various applications | Improves user experience by streamlining logins |
| Passwordless | Eliminates password-based vulnerabilities | Can be challenging to implement and maintain; user adoption | Highest level of security; potentially streamlined user experience |
This table summarizes the benefits, challenges, and user experience impacts of different authentication methods. By weighing these factors, organizations can choose the most suitable approach for their particular needs and resources.
Ready to improve your team's security and move beyond the risks of password sharing? Explore AccountShare today and discover how our platform helps teams securely access and manage shared accounts: Learn more about AccountShare.
