
Remote Work Security Solutions Your Business Guide
Share
Think of remote work security less as a single product and more as a complete mindset—a collection of tools, policies, and practices designed to keep your company's data safe, no matter where your team is working. When employees step outside the traditional office, they also step outside its built-in security perimeter. This creates new vulnerabilities, from unsecured home Wi-Fi networks and personal devices to clever phishing attacks that prey on the isolated worker.
In essence, you're building a modern defense system for a business that no longer has physical walls.
Why Remote Work Security Is Non-Negotiable

The move to remote and hybrid work wasn't just a temporary trend; it fundamentally broke the old security model. For decades, companies operated on a simple principle: trust what's inside the office network, and scrutinize everything outside. Your sensitive data was protected by a single, heavily fortified digital wall.
Today, that data is being accessed from hundreds of different locations, each with its own set of risks. This new reality demands a complete overhaul of how we think about security. It's no longer just an IT issue—it's a core business strategy that’s absolutely critical for survival.
The New Digital Kingdom
Imagine your business used to be a castle, surrounded by a massive wall with a single, heavily guarded gate. Anyone who needed access had to come through that one point, where their identity was checked and their intentions were verified.
Now, picture your business as a sprawling kingdom with hundreds of outposts scattered across the country, or even the globe. Each outpost—an employee’s home office, a coffee shop, or a co-working space—is a potential entry point for an attacker. Leaving these outposts undefended is simply not an option.
Protecting this distributed kingdom isn't about building taller walls around the old castle. It's about giving each individual outpost its own set of defenses—from encrypted communication lines to vigilant security on every single device.
Understanding the Urgency
The numbers tell a story of incredible urgency. The global remote work security market was valued at a staggering USD 56.15 billion in 2024 and is on track to hit USD 173.66 billion by 2030. You can dig into the specifics in the full report from Grand View Research. This explosive growth isn’t just about new technology; it highlights a massive, enterprise-wide race to plug the security gaps created by decentralized work.
Failing to adapt leaves your business wide open to the very threats that cybercriminals are actively exploiting every single day.
To build an effective defense, you need a multi-layered approach. The table below breaks down the essential pillars of a modern remote work security strategy, showing what each component does and the specific risks it helps neutralize.
Core Components of a Modern Remote Work Security Strategy
| Security Component | Primary Function | Key Risk Mitigated |
|---|---|---|
| Virtual Private Network (VPN) | Creates a secure, encrypted tunnel over the internet. | Data interception on public or unsecured Wi-Fi. |
| Endpoint Security | Protects individual devices (laptops, phones) with antivirus, firewalls, and monitoring. | Malware, ransomware, and unauthorized device access. |
| Identity & Access Management (IAM) | Verifies user identities and enforces access permissions (e.g., MFA, SSO). | Stolen credentials and unauthorized access to sensitive systems. |
| Data Encryption | Scrambles data both at rest (on a hard drive) and in transit (over the network). | Data theft from lost/stolen devices or network snooping. |
| Security Monitoring & Logging | Continuously tracks network and system activity to detect suspicious behavior. | Undetected breaches, insider threats, and policy violations. |
| Security Policies & Training | Establishes clear rules for secure remote work and educates employees on threats. | Human error, phishing attacks, and accidental data exposure. |
A robust strategy isn’t about picking just one of these; it's about weaving them together into a cohesive defense. A multi-layered approach is no longer a luxury for large enterprises—it's a baseline necessity for protecting your assets and your reputation in this new era of work. This guide will give you a clear roadmap for building that defense.
What Are We Really Up Against? The Modern Threat Landscape
Before you can build a solid defense, you have to know what you're fighting. The threats hitting today’s remote teams aren't just vague digital bogeymen; they're specific, well-planned attacks that prey on the unique weak spots of a scattered workforce. Cybercriminals have gotten smarter, shifting their focus to the most predictable vulnerability: the human element and the hodgepodge of personal networks we all use.
The old idea of a secure corporate "perimeter" is completely gone. Think about it—every employee's home network is now a potential backdoor into your company, and every personal phone checking work email is a target. This isn’t just a what-if scenario; it's the daily reality for organizations of all sizes.
From Clever Phishing to Shaky Home Networks
The ways attackers can get in have multiplied. They know remote employees are often juggling more distractions, can't just lean over and ask a coworker "Hey, does this email look weird?", and are almost entirely dependent on digital messages. It's a perfect storm for them to exploit.
Here are a few of the biggest culprits targeting remote workers:
- Deceptively Real Phishing: We're not talking about those old, poorly-worded spam emails anymore. Attackers now send convincing messages that look like they’re from your IT department, HR, or even the CEO. They create a false sense of urgency—"Urgent: Remote VPN access issue"—to trick people into handing over their logins without thinking twice.
- Unsecured Home Wi-Fi: Let’s be honest, how many people change the default password on their home router? Or keep its software updated? Attackers know this, making home networks low-hanging fruit. Once they’re in, they can watch all the internet traffic, steal sensitive information, and even jump from the home network to a connected company laptop.
- Vulnerable Personal Devices (BYOD): When staff use their own laptops or phones for work, they bring a whole new set of risks. These devices might not have the latest security updates, could be infected with malware from personal browsing, or are sometimes shared with family members. Each one is an uncontrolled gateway right into your company’s data.
The move to remote work wasn't just a logistical shift; it was a security earthquake. A staggering 92% of IT professionals believe that teleworking has cranked up the security risks for their companies. And it's not just a feeling—nearly four out of five businesses (78%) have dealt with at least one security incident directly linked to a remote worker. If you want to see the full picture, you can find more remote work security stats that break down the full scope of these emerging threats.
A Coffee Shop Mistake Can Become a Company Crisis
Let's paint a quick, and all-too-common, picture. An employee is working from a coffee shop and connects to the public Wi-Fi to quickly check some emails. On that same network, an attacker is lurking and uses a "man-in-the-middle" attack to snatch the employee's login credentials as they access a cloud service. Crucially, that account isn't protected by Multi-Factor Authentication (MFA).
Within minutes, the attacker is in your system. They don't set off any alarms. Instead, they move silently, exploring your network for anything valuable. They discover a cloud folder full of customer data that wasn't configured correctly and quietly copy everything. The breach isn't discovered for weeks.
It all started with one insecure connection and one missing layer of security. That’s how fast a small oversight can spiral into a massive data breach, and it’s exactly why you can’t afford to be reactive.
Building Your Foundational Security Pillars
To truly secure a distributed workforce, you can't just rely on policies. You need a set of core technologies that act as the foundational pillars of your security. Think of them as the essential building blocks that work together to protect your data, devices, and people.
Without these pillars firmly in place, any remote work security strategy is going to have some serious weak spots—the kind that attackers are always looking to exploit. Each pillar tackles a specific vulnerability, creating a defense that has multiple layers. When you bring them all together, you get a solid framework that can stop common cyberattacks in their tracks.
Let's break down the three most crucial ones every organization needs.
1. VPNs: Your Private Data Tunnel
The first pillar is the Virtual Private Network (VPN). Picture this: your remote employee is working from a coffee shop, sending sensitive company data over the public Wi-Fi. Without any protection, that data is like a postcard that anyone on the network can pick up and read.
A VPN fixes this by creating a private, encrypted tunnel right through the public internet. It’s like sending your data in an armored, windowless vehicle instead of an open-air convertible. Even if a cybercriminal is lurking on the same network, all they see is the armored vehicle driving by; the contents inside are completely hidden and secure. This is the absolute first step in protecting data in transit for any remote employee.
The infographic below shows some of the most common ways attackers go after remote workers, which really drives home why tools like VPNs are so critical.
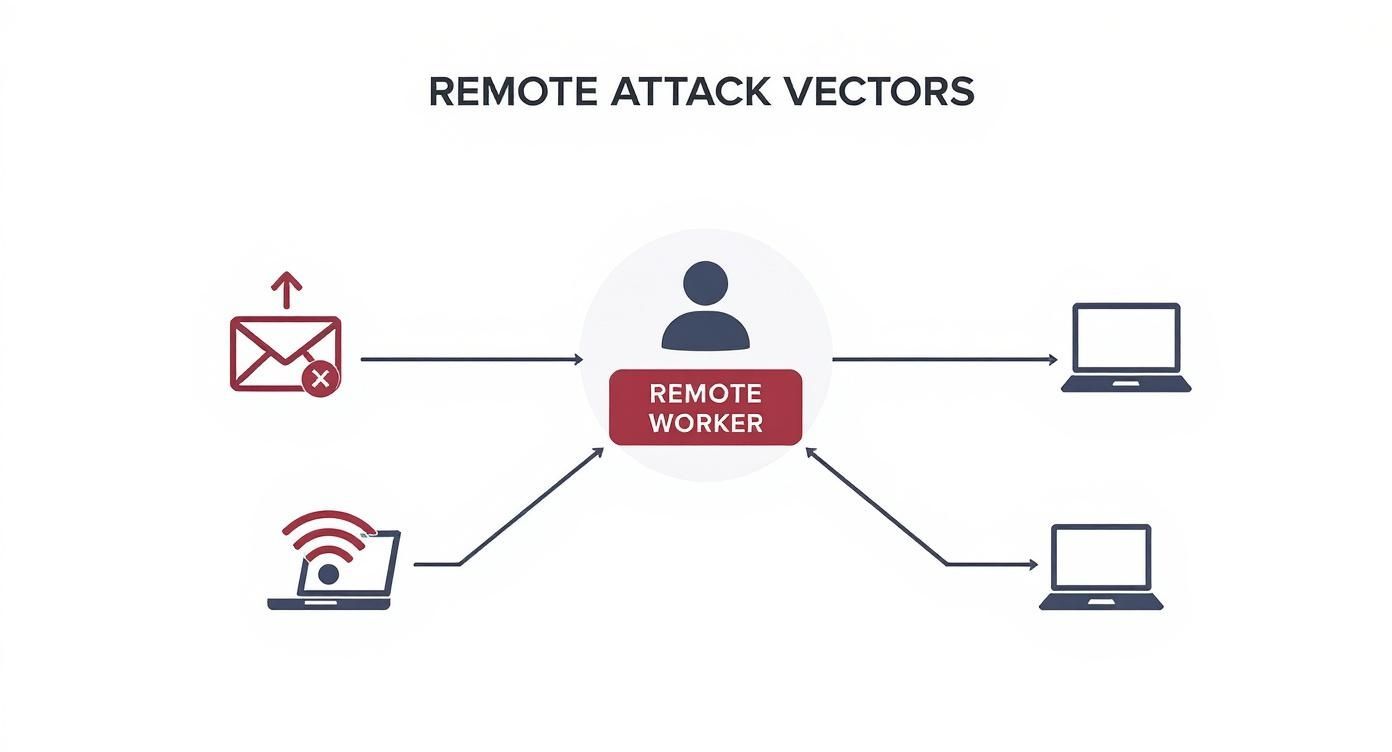
As you can see, things like phishing, unsecured networks, and personal devices all create direct paths for attackers. This is exactly why a layered defense is non-negotiable.
2. Identity and Access Management: The Digital Gatekeeper
A VPN secures the connection, but it doesn't verify who is using it. That’s where Identity and Access Management (IAM) comes into play. Think of IAM as the digital gatekeeper for your company’s resources, making sure only the right people get access to the right information, and only when they need it.
The most effective part of any modern IAM strategy is Multi-Factor Authentication (MFA). If a password is like a key to a door, MFA is the extra step—like a secret handshake or an ID check—you need before the door will open. It forces a user to provide two or more verification factors to get into an application or system.
This usually involves a combination of:
- Something you know (a password)
- Something you have (a code from your phone)
- Something you are (a fingerprint or face scan)
By requiring that second form of proof, MFA can block over 99.9% of account compromise attacks. Even if a criminal steals an employee's password in a phishing scam, they're stopped cold because they don't have the employee's phone to approve the login.
Getting IAM configured correctly is a cornerstone of modern security. To get a better sense of the different strategies, it's worth learning more about the various access control methods and how they fit into different situations.
3. Endpoint Detection and Response: The Vigilant Device Guard
Our final foundational pillar is Endpoint Detection and Response (EDR). An "endpoint" is simply any device that connects to your network—laptops, tablets, smartphones. Every single one is a potential entry point for malware or ransomware. A VPN can't stop a user from accidentally downloading a malicious file, and MFA can't help once malware is already running on a machine.
That’s where EDR steps in. Think of it as a vigilant, always-on security guard stationed on every single company device. It doesn't just scan for known viruses like old-school antivirus software. Instead, it constantly monitors device activity for anything that looks suspicious.
For instance, if an employee’s laptop suddenly starts encrypting files at an insane rate (a classic sign of ransomware), an EDR solution spots this behavior instantly. It can then take immediate, automated action—like isolating that device from the network—to stop the ransomware from spreading to other systems. That rapid response can be the difference between a minor incident on one computer and a catastrophic breach that shuts down the entire company.
Together, these three pillars—VPNs, IAM with MFA, and EDR—form the bedrock of effective remote work security solutions, creating a layered defense that protects your company from every angle.
Embracing a Zero Trust Security Mindset

The security tools we’ve covered are crucial, but they’re most effective when guided by the right philosophy. For years, the standard was "trust but verify"—a model that assumed anyone inside the company network was probably safe. That idea is officially obsolete.
In today's world where the "office" can be anywhere, we need a smarter, more skeptical approach. That's where the Zero Trust model comes in. It’s not a product you buy off the shelf; it's a fundamental shift in how you think about security. The core principle is simple but powerful: never trust, always verify.
This model operates on the assumption that a threat could come from anywhere, both outside and inside your network. It accepts that a breach is a matter of when, not if. As a result, every single request to access a company resource is treated with suspicion until it's properly authenticated, authorized, and encrypted.
The Core Tenets of Zero Trust
A Zero Trust architecture isn't built on a single defense but on several key concepts working in harmony. It's not just about who is trying to connect, but also what they’re trying to do, from where, and on what kind of device. This granular approach is the bedrock of any solid remote work security strategy.
The three main pillars of this strategy are:
- Continuous Verification: Zero Trust is constantly checking. Just because someone logged in this morning from a company laptop doesn't grant them a free pass for the rest of the day. If that laptop suddenly shows signs of a malware infection, its access is cut off instantly.
- Least-Privilege Access: This is all about giving people the absolute minimum access they need to do their jobs, and nothing more. Someone in marketing has no business being in the company's financial databases, so their access to those systems is blocked by default.
- Micro-segmentation: Think of your network as a big, open-plan office. If one person gets sick, it's easy for the germs to spread everywhere. Micro-segmentation is like building secure, contained offices for each department. If one area is compromised, the breach is sealed off and can't spread to the rest of the company.
A Zero Trust model changes the fundamental security question from "Are you on our network?" to "Are you a verified user, on a healthy device, with explicit permission to access this specific resource right now?" This tight control dramatically shrinks the blast radius of any potential attack.
How Zero Trust Works in the Real World
Let's walk through a real-world scenario. A hacker manages to steal an employee’s password through a clever phishing email. In a traditional security setup, that might be all they need to wander through the corporate network.
With Zero Trust, their attack hits a brick wall almost immediately.
First, the attacker tries to log in with the stolen credentials. They're instantly challenged with a Multi-Factor Authentication (MFA) prompt on the employee’s phone, which, of course, they don't have. Dead end.
But let's say they somehow found a way around MFA. Their next moves are still severely restricted.
When they try to access a critical database, the system checks their permissions. The credentials belong to someone in sales, so the principle of least privilege kicks in and denies them access to engineering servers. At the same time, the system flags the login as suspicious because it’s coming from an unrecognized device in a strange location.
This layered, verify-everything approach is no longer optional; it's essential. A solid identity and access management system is the backbone of this model, and you can explore different identity management solutions to see how they enforce these rules. To really get under the hood of this paradigm, the concept of "Zero Trust Security" is a great place to start.
Creating a Culture Of Security Awareness
Even the strongest security tools can collapse around a single human slip. Think of your technology as the walls of a fortress—and your team members as the sentries on patrol. Turning them into vigilant defenders isn’t just a smart move; it’s absolutely necessary.
Building that mindset means moving past the annual training video and weaving security into every workday. When people feel like partners in safeguarding key systems and data, they respond differently. They ask questions, spot odd messages, and raise alarms without hesitation.
Moving Beyond Annual Checkboxes
Compliance shouldn’t be the finish line. Instead, aim for real, lasting behavior change by making training engaging and directly tied to your current risks.
A robust program might include:
-
Realistic Phishing Simulations
Send regular, well-crafted fake phishing emails. You’ll see who clicks first and what tactics most often fool your team. -
Ongoing Micro-Learning
Drop two-minute videos, quick tips in Slack, or bite-sized reminders in newsletters. These little nudges stick far better than a 60-minute webinar. -
Clear, Simple Policies
Rewrite your Acceptable Use Policy (AUP) in straightforward language. People need to know exactly how to handle data, personal devices, and public Wi-Fi—no legalese allowed.
When an employee feels comfortable saying, “This email looks off—can someone check?” you’ve unlocked your best threat detector.
Empowering The Human Firewall
Training has to be more than theory. Give your team practical steps they can follow, both at work and at home. That way, security stops feeling like a mandate and starts feeling like a habit.
Key Focus Areas
-
Strong Password Hygiene
Explain why reuse is risky. Encourage a password manager and unique, complex passwords for every account. -
Securing Home Networks
Offer a simple guide: change that default router admin password, switch on WPA3 encryption, and keep firmware up to date. -
Physical Device Security
Remind people about the dangers of public spaces. A privacy screen on a laptop and never leaving devices unattended can save you from data theft—or worse, stolen hardware.
By making each lesson personal and practical, security becomes a shared responsibility rather than a chore. When everyone feels they have a stake in the outcome, your defense grows stronger—one person at a time.
Choosing Your Remote Work Security Solutions
Moving from theory to practice—from understanding security concepts to actually picking the right tools—can feel like a huge leap. It's easy to get overwhelmed by the sheer number of vendors and technologies all promising to solve your problems. The secret? Start with your business needs, not a product catalog.
A solid assessment of your current reality is the only way to choose remote work security solutions that will actually protect your company without grinding productivity to a halt. Take an honest look at your setup. Who are your employees? What kind of data are they touching, and where are they doing it from? A small startup with five remote developers has a completely different risk profile than a large healthcare system with hundreds of clinicians accessing patient records from their homes.
Frame Your Decision Making Process
To keep from getting lost in a sea of technical jargon, focus on the big-picture factors that will truly make or break a solution's success. Your goal isn't just to find powerful tools, but practical ones that fit into your specific world.
Start by asking a few fundamental questions:
- Scalability: Will this solution grow with us? A tool that’s perfect for 20 employees might completely fall apart under the pressure of 200.
- User Experience: How will this impact our non-technical staff? If a security measure is too complicated, people will find ways around it, and those workarounds open up brand new security holes.
- Integration: How well does this play with our existing IT stack? The best tools don't create more silos; they connect seamlessly with the software you already rely on, building a single, unified defense.
A successful security strategy isn't a one-and-done purchase. It's an ongoing journey of adaptation. The right solutions are the ones that let you build a resilient, future-proof defense that can evolve as new threats pop up.
Building Your Selection Checklist
The market for these tools is exploding as businesses everywhere scramble to adapt. By 2033, the global remote work security market is projected to skyrocket past USD 390 billion, a massive leap from USD 54.8 billion in 2023. This growth really highlights how critical secure remote work has become, especially for companies in heavily regulated fields like finance and healthcare. For a detailed breakdown of this trend, you can find more insights about the remote work security market.
As you start looking at vendors, use a simple checklist to keep your decision-making on track:
- Assess Core Functionality: Does this tool actually solve your biggest security gap? Whether it's protecting laptops, verifying identities, or locking down connections, make sure it does the main job well. Our secure remote access guide can help you figure out what to tackle first.
- Evaluate Vendor Support: What happens after you sign the contract? Find out what kind of support and training the vendor provides, both during setup and for the long haul.
- Review Total Cost of Ownership: Don't just look at the sticker price. Factor in the ongoing costs for maintenance, training, and any headaches that might come with integrating it into your systems.
Since so much of modern remote work relies on the cloud, getting a handle on cloud security is essential. For a deep dive, the AWS Certified Security Specialty Study Guide is an excellent resource. By systematically thinking through these factors, you can move forward with confidence and choose the tools that truly align with your business goals and security needs.
Got Questions About Remote Security? We've Got Answers.
When you're trying to lock down a workforce that's spread all over the map, you're bound to have questions. It's totally normal. Getting the right answers is what turns a good plan into a great one, so let's dig into some of the most common things people ask.
Think of this as a quick chat to clear up the confusion between knowing the risks and actually putting the right defenses in place.
"Is a VPN enough to keep my remote team secure?"
A VPN is a fantastic start, but it's not the whole story. Imagine a VPN as a private, armored tunnel for your company's data to travel through on the internet. It's great for hiding the traffic from outsiders, but it doesn't check the car driving through the tunnel for problems or confirm the driver is who they say they are after they've entered.
For real security, you need layers. The VPN handles the connection, but you also need something like endpoint protection to make sure the laptop itself is clean, and multi-factor authentication (MFA) to continuously prove your team members are who they claim to be. Just relying on a VPN leaves the door open for other kinds of attacks.
"What's the single biggest security mistake companies make with remote work?"
Hands down, the most dangerous slip-up is assuming an employee's home network is safe. It’s easy to forget that a company laptop is sharing a Wi-Fi network with personal smart speakers, gaming consoles, and other family members' computers—any of which could be a weak link. Attackers love using these unsecured devices as a backdoor to get to a corporate device.
The only way to counter this is to adopt a Zero Trust mindset. It's simple, really: trust no one. Treat every connection, even from a trusted employee's home, as potentially hostile. This forces you to focus on securing the device itself and verifying the user's identity every time, no matter where they are.
This simple shift in perspective means a compromised home router doesn't automatically become a company-wide disaster.
"How can we add more security without slowing everyone down?"
This is the million-dollar question, and the answer is all about the user experience. If security is a pain, your team will find ways around it—and those workarounds are almost always risky. The trick is to pick modern remote work security solutions that are so smooth, people barely notice them.
Here’s how you can strike that perfect balance:
- Use push notifications for MFA. A simple tap on a phone is so much better than digging for a six-digit code.
- Roll out Single Sign-On (SSO). One strong password to access everything is a win-win. It cuts down on password headaches for your team and gives you a central point of control.
- Train your people well. Don't just give them rules; explain why the rules exist. When people understand that security is there to protect them and the company, it stops feeling like a roadblock.
When security feels easy and intuitive, people just do it.
"We need to get better at this. What's the very first step?"
Start with a solid risk assessment, but focus it entirely on your remote team. You can't protect what you can't see. Your first job is to map out every device, app, and piece of data being accessed from outside the office. This will shine a spotlight on your biggest vulnerabilities.
Once you have that map, you'll know exactly where to start. For most organizations, the single best thing you can do right away is to enforce multi-factor authentication (MFA) on every important system. It's a relatively simple change that immediately shuts down the most common type of attack: stolen passwords.
At AccountShare, we get it. You need access to be both secure and simple. Our platform is built to help you manage shared premium services without the headaches, making sure your team can collaborate and save costs without compromising on security. Find a smarter way to share at https://accountshare.ai.
