
A Guide to Access Control Methods
Share
Think of your organization's digital resources as a highly secure building. Access control methods are the rules that decide who gets which keys. Does someone get a master key that opens every door, or just a key to a specific floor, or maybe only a single key for one office? These are the digital policies that determine who can view, use, or alter your most important assets.
Why Access Control Methods Matter
At its heart, access control is the security practice of managing who can interact with what. It’s the bouncer for your company's data, applications, and systems. Without a solid plan, you're leaving sensitive information—customer lists, financial records, proprietary code—wide open for the taking.
A good access control strategy is built on a simple but powerful idea: the principle of least privilege (PoLP). This means people should only have the absolute minimum access they need to do their jobs. An accountant doesn't need entry to the software development environment, and a developer has no business poking around in payroll. Enforcing this principle drastically shrinks your attack surface.
The Growing Importance of Access Security
Mismanaging access is one of the biggest security headaches for companies today. It's a direct line to data breaches, compliance violations, and serious financial damage. This risk is fueling massive growth in the security market.
The global access control market, currently valued around USD 19.05 billion, is expected to skyrocket to USD 61.31 billion by 2035, a clear sign that businesses are scrambling for better security. You can dig into the numbers and trends in this market analysis from Future Market Insights.
This guide will walk you through the most common access control methods, breaking down how they work and where they shine. By the end, you'll have a much clearer idea of which approach fits your own needs.
"The goal of access control isn't just to keep the wrong people out. It's to make sure the right people have exactly the access they need, right when they need it—and absolutely nothing more."
Let's start exploring the different models so you can make smart decisions to protect your digital world. For a more foundational look, be sure to read our guide on what is access control and why you need it, which sets the stage for the specific models we'll cover next.
Discretionary and Mandatory Access Control (DAC and MAC)

Before we can dive into the sophisticated security models of today, we have to go back to the beginning. The two original blueprints for managing access are Discretionary Access Control (DAC) and Mandatory Access Control (MAC). Think of them as the foundational philosophies that have shaped everything that followed.
At their core, they represent two completely different ways of thinking about who gets to decide who sees what. One method puts that power directly into the hands of users, while the other locks things down with a rigid, system-wide set of rules.
Discretionary Access Control Explained
Discretionary Access Control, or DAC, is probably the model you're most familiar with, even if you don't know it by name. If you've ever shared a Google Doc, given a colleague access to a Trello board, or changed permissions on a Dropbox folder, you've used DAC.
In a DAC system, the owner of an object—be it a file, folder, or database—has the discretion to decide who can access it. They can grant or revoke permissions to other users whenever they want, essentially creating a custom access list for that specific resource.
This approach makes DAC incredibly flexible and user-friendly. It's built for collaboration. The people creating the work are empowered to share it with the people who need it, without having to jump through administrative hoops.
But that flexibility is a double-edged sword. Its biggest strength is also its greatest weakness. Security rests entirely on individual users making smart, consistent choices. When someone accidentally gives "editor" access to the wrong person or forgets to remove a contractor's access after a project ends, a major security hole is created.
Mandatory Access Control Explained
On the complete opposite end of the spectrum, we have Mandatory Access Control, or MAC. This model is all about strict, centrally managed rules that no single user can override—not even the person who created the resource.
The classic example is a military or government intelligence setting. Here, information is rigorously classified. Your ability to access a document isn't determined by who wrote it. Instead, it's based on a system-wide policy that assigns security labels to everything: users get a clearance level (like "Secret") and resources get a classification level (like "Top Secret").
A user with "Secret" clearance can see files classified as "Secret" or below, but they are completely blocked from anything labeled "Top Secret". It doesn't matter who created the file or if they want to share it. The system administrator sets these rules, and the system itself enforces them.
The core principle of MAC is simple: the system enforces security, not the people. This removes human error from the equation, providing the highest level of information protection for sensitive environments.
Because it’s so rigid and unyielding, MAC just isn't practical for most collaborative business environments. You'll find it almost exclusively in government agencies, military operations, and other high-stakes organizations where preventing an information leak is the number one priority.
Comparing DAC and MAC
To really see the difference, let’s put them side-by-side.
| Feature | Discretionary Access Control (DAC) | Mandatory Access Control (MAC) |
|---|---|---|
| Control | Owner of the resource | System administrator |
| Flexibility | High (users can share freely) | Low (rigid, system-wide rules) |
| Security | Lower (depends on user decisions) | Highest (centrally enforced) |
| Common Use | Commercial businesses, cloud storage | Military, government, high-security |
It all boils down to a fundamental trade-off between usability and security. DAC champions ease of use and collaboration, which is perfect for most businesses. MAC prioritizes airtight security above all else, making it the only choice when a data breach could be catastrophic.
Understanding which approach, or modern hybrid, is right for you depends entirely on your organization's risk profile and operational needs. For a deeper look at how permissions are actually assigned in practice, you can explore our complete guide to user roles and permissions to see these concepts in action. While platforms like AccountShare often rely on newer, more flexible models, a solid grasp of DAC and MAC is essential for understanding the DNA of all modern access control.
Organizing Permissions with Role-Based Access Control (RBAC)

While the Discretionary and Mandatory models lay the groundwork, most organizations today need something that marries strong security with day-to-day practicality. That’s exactly where Role-Based Access Control (RBAC) comes in. It has become the absolute workhorse for corporate security, and for good reason—it’s both powerful and refreshingly intuitive.
Think about a hospital for a moment. Imagine the chaos of trying to grant access rights one-by-one to every single doctor, nurse, and administrator who walks through the door. It would be a nightmare of mistakes and security holes.
RBAC flips that script. Instead of focusing on individuals, you create roles that mirror their actual jobs.
A 'Doctor' role, for instance, gets permission to see patient charts and lab results. A 'Pharmacist' role can look at medication inventories and prescriptions, while a 'Billing' role is restricted to financial data. When a new doctor joins the team, you just assign them the 'Doctor' role. Boom. They instantly get all the permissions they need to do their job—no more, no less.
The Core Components of RBAC
This approach is so effective because it builds a logical bridge between people and permissions, making security management far simpler. The whole system is built on three straightforward, connected parts:
- Users: These are the individuals who need to get into the system, like Dr. Smith, Nurse Jones, or Mark from accounting.
- Roles: These are just collections of permissions grouped by job function or responsibility. Think 'Administrator,' 'Editor,' 'Project Manager,' or 'Read-Only Viewer.'
- Permissions: These are the specific actions a role is allowed to take, such as 'create document,' 'delete user,' 'view report,' or 'edit database entry.'
With RBAC, you never assign a permission directly to a user. You assign users to roles, and those roles already have their permissions baked in. This separation is the secret sauce to its efficiency and scalability.
By grouping permissions into logical roles, RBAC enforces the principle of least privilege in a structured way. It ensures users only get the access they need for their job function, which significantly reduces the risk of both accidental data exposure and malicious insider activity.
This organized framework is precisely why RBAC is one of the most widely researched and adopted access control methods, especially in complex places like healthcare and massive enterprises. Its design simply offers better scalability and administrative sanity than older models. For a deeper dive, you can explore its evolution and impact on enterprise systems.
RBAC in a Business Setting
Let's bring this into a typical business. Picture a marketing team using a project management tool.
Instead of fiddling with permissions for every team member, an administrator can just set up a few core roles:
- Marketing Manager: Can create new projects, assign tasks to anyone, view all team reports, and approve budgets.
- Content Writer: Can create and edit documents within their assigned projects, comment on tasks, and upload files. They can't delete projects or see budget details.
- Freelance Designer: Can only view tasks assigned directly to them and upload finished designs to a specific folder. They are locked out of all other projects and team chatter.
When a new content writer is hired, the admin just gives them the 'Content Writer' role. Instantly, they have everything they need to get started. And when that freelancer's contract is up? Their role is revoked, and all access is shut off immediately and completely.
The Major Benefits of RBAC
This method brings beautiful order to what could easily be a permissions mess. Its advantages make it the go-to choice for organizations of all sizes, including platforms like AccountShare that help manage group access.
- Simplified Administration: Managing a handful of roles is worlds easier than managing thousands of individual permissions. This is a massive time-saver for any admin.
- Enhanced Security: By sticking to the principle of least privilege, RBAC shrinks your attack surface. An attacker who compromises a 'Content Writer' account can't approve phony invoices.
- Improved Compliance: Many regulations (like SOX and HIPAA) demand that you prove who has access to sensitive data. RBAC creates a clear, auditable trail based on job roles, making compliance checks much less painful.
- Scalability: An organization can grow from 10 employees to 10,000, but the number of core roles might barely change. RBAC handles that kind of growth effortlessly, without burying your security team.
Of course, RBAC isn't a silver bullet. It can feel a bit rigid if roles are defined too broadly, and it sometimes struggles in highly dynamic environments where access needs depend on real-time context, not just a job title. For those ultra-specific scenarios, you might need an even more granular model.
Of course. Here is the rewritten section with a more natural, human-expert tone.
Using Context with Attribute-Based Access Control (ABAC)
If Role-Based Access Control (RBAC) is about assigning permissions based on job titles, then Attribute-Based Access Control (ABAC) is like having a hyper-aware security guard who asks, "Okay, but what's the full story here?" ABAC is the most dynamic and fine-grained of all the major access models, making decisions not just on who you are, but on the real-time context of your request.
Think of it like a smart security system for a high-tech lab. Your keycard (your role) isn't enough to get you in. The system also checks: Is it business hours? Are you on the approved project list for this specific lab? Are you trying to access a sensitive experiment or just the coffee machine? That’s ABAC in a nutshell—it uses a rich set of data points to make smarter, more precise access decisions on the fly.
The Core Idea Behind ABAC
ABAC shifts the focus from static roles to a more fluid, rule-based system. It grants or denies access by evaluating policies against the attributes of the user, the resource they want, the action they're trying to take, and the environment they're in.
This approach gives you an incredible level of control that's nearly impossible to get with RBAC alone. It's the engine that powers modern security philosophies like Zero Trust, where you never assume trust and have to verify every single access attempt.
At its heart, ABAC doesn't ask, "Is this person an Admin?" It asks something much more detailed: "Does this user, with these specific attributes, trying to perform this action on this resource, under these current conditions, match our security policy?" This leap from static roles to dynamic rules is what makes it so powerful.
The Four Pillars of ABAC
So, how does ABAC actually work? It all comes down to combining information from four key categories. Think of these as the building blocks for creating any access rule.
- User Attributes: Who is making the request? This isn't just their role. It could be their security clearance, their department, what training they've completed, or even their physical location.
- Resource Attributes: What are they trying to access? This describes the data or system itself. Think of things like a file's creation date, its sensitivity level (e.g., 'Public,' 'Confidential'), the project it belongs to, or whether it contains personal information (PII).
- Action Attributes: What are they trying to do? This is the verb of the request—'read,' 'write,' 'edit,' 'delete,' 'approve,' or 'download.'
- Environmental Attributes: What’s the context? This is where the real-time intelligence comes in. It includes factors like the time of day, the user's geographic location, the type of device they're using, and the security of their network connection.
By mixing and matching these four pillars, you can craft some seriously specific security policies.
ABAC in Action: A Real-World Scenario
Let's bring this to life with an example. Picture a hospital where a doctor needs to view a patient's electronic health record (EHR).
An ABAC policy would sound something like this:
"Allow access IF..."
- User Attribute: The user’s role is 'Doctor' and their name is listed as the patient's primary care physician.
- Resource Attribute: The record being accessed is classified as 'Patient Medical Record.'
- Action Attribute: The action being requested is 'read' or 'view.'
- Environmental Attribute: The request is coming from a hospital-owned device on the internal network and it's during the doctor's scheduled shift.
If even one of those conditions isn't met—if the doctor tries to delete the file, is logging in from a public Wi-Fi network, or isn't the assigned physician for that patient—access is automatically blocked. This is why ABAC is the gold standard for complex, high-stakes environments.
The Trade-Offs: Complexity vs. Granularity
The biggest win for ABAC is its incredible flexibility and granular control. It can be molded to fit almost any security need, which is perfect for fast-moving organizations where roles and projects are always changing. For a group-sharing platform like AccountShare, ABAC could be used to create a policy like: "allow a team member to use a shared software license only from a company-issued laptop and only for the duration of their active subscription."
But all that power comes with a price tag: complexity. Designing, building, and maintaining an ABAC system is no small feat. You have to meticulously define all the attributes and then write the complex logic that ties them all together. This requires serious planning and often specialized expertise. A poorly configured ABAC system can be a nightmare, either leaving gaping security holes or, just as bad, locking out legitimate users who need to get their work done.
While RBAC gives you a solid foundation of organized, role-based permissions, ABAC takes it to a whole new level by adding real-time context into the mix. For any organization that needs the highest degree of adaptive security, the investment in ABAC can be well worth it.
How to Choose the Right Access Control Model
Knowing the theory behind different access control models is one thing. Actually picking the right one for your business? That’s where the real work begins. This isn't just a technical checkbox to tick; it's a strategic decision that forces you to balance tight security, operational flexibility, and the day-to-day workload for your team.
Let's make this real. Imagine you need to give a freelance designer temporary access to a single project folder on your company’s server. They need to upload their files, but that's it—they absolutely should not see anything else.
How would each of the major access control models handle this everyday request?
A Scenario-Based Comparison
Let's walk through how each model would fare in this scenario. You'll quickly see their unique personalities—and their pros and cons—come to life.
-
Discretionary Access Control (DAC): The project manager, as the owner of the folder, could give the designer direct access. It’s quick and simple. The problem? It’s also a security headache waiting to happen. The manager could easily grant permissions that are too broad or, more likely, forget to revoke access when the project is over, leaving a door wide open.
-
Mandatory Access Control (MAC): This would be total overkill and frankly, unusable for this situation. MAC’s rigid, top-down rules are built for highly sensitive environments like intelligence agencies, not for nimble collaboration with contractors. You can't just create a new system-wide security classification for a single freelancer.
-
Role-Based Access Control (RBAC): Here, an administrator would create a "Freelance Designer" role. This role would have permissions locked down to only allow reading and writing within designated project folders. It's secure, predictable, and scales well. The only catch is the administrative overhead of creating and managing a new role just for a temporary worker.
-
Attribute-Based Access Control (ABAC): This is where things get really smart. An admin could set a policy that says something like: "Allow any user with the attribute 'Contractor: Designer' to write to folders with the attribute 'Project: Active' but only between their contract start and end dates." Access is granted and then disappears automatically based on these real-time attributes.
The trade-offs become crystal clear. DAC gives you speed but at the cost of good security hygiene. RBAC brings structure and safety but can feel a bit rigid for one-off needs. ABAC provides incredibly precise, automated control, but it does require more thought and effort to set up initially.
This visual breakdown captures how these models stack up on key metrics like security, complexity, and cost.
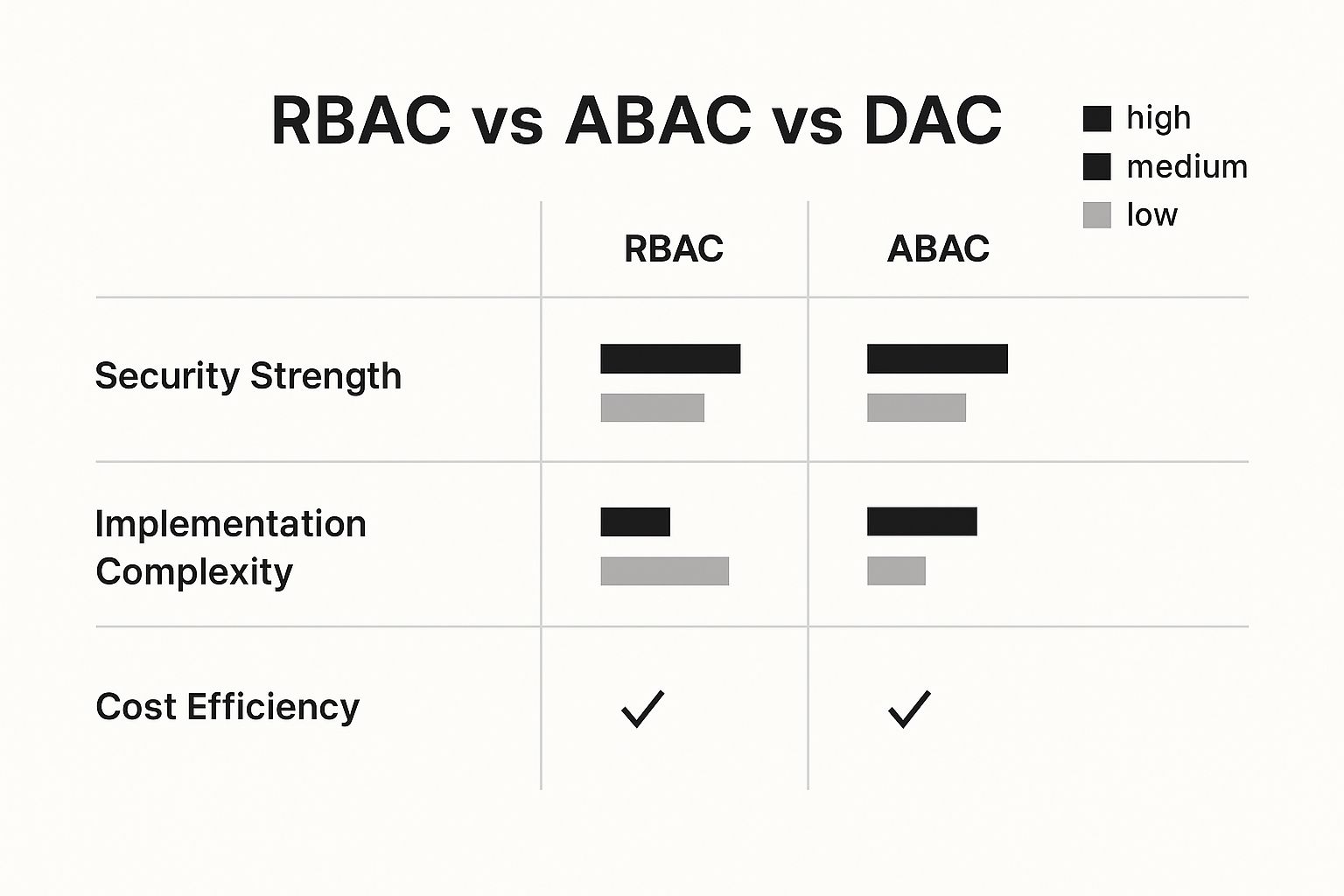
As you can see, the most powerful and flexible models often demand more during implementation. This means you have to make a conscious choice based on what your organization truly values and can support.
Access Control Model Comparison Matrix
To help you visualize the differences more clearly, here is a direct comparison of the main models across several important criteria. This matrix breaks down how each one stacks up in terms of flexibility, management, and security focus, making it easier to see which approach aligns with your needs.
| Criterion | Discretionary (DAC) | Mandatory (MAC) | Role-Based (RBAC) | Attribute-Based (ABAC) |
|---|---|---|---|---|
| Control | Owner-centric | System-centric | Role-centric | Policy-centric |
| Granularity | Low | Low (based on labels) | Medium (based on roles) | High (dynamic attributes) |
| Flexibility | High | Very Low | Medium | Very High |
| Management | Decentralized, simple | Centralized, complex | Centralized, moderate | Centralized, complex policies |
| Scalability | Poor | Good for static systems | Good | Excellent |
| Best For | Small teams, non-critical data | Government, military | Enterprises with defined roles | Dynamic, complex environments |
This side-by-side view highlights the fundamental trade-offs. While DAC is simple, it doesn't scale. MAC is secure but inflexible. RBAC offers a great middle-ground for many businesses, while ABAC provides the ultimate in dynamic, fine-grained control for those who can manage its complexity.
Making the Final Decision
So, how do you pull the trigger and choose? Your decision should really come down to answering a few honest questions about your organization.
Choosing an access control model is about finding the sweet spot between airtight security and operational agility. You need a system that protects your assets without preventing your team from doing their work efficiently.
Think through these factors before you commit to a model:
- Your Security Needs: Are you protecting public marketing assets or state secrets? The more sensitive the data, the more you should lean toward the structure of RBAC or the highly granular control of ABAC.
- Your Organizational Complexity: How big is your team? A 5-person startup might do just fine with a simple DAC-like approach. But a company with 500 employees across 10 departments will find RBAC absolutely essential for maintaining sanity and order.
- Your Administrative Resources: Do you have a dedicated IT or security team ready to manage complex policies? ABAC is incredibly powerful, but it’s not a "set it and forget it" tool. Be realistic about the people and time you can dedicate to ongoing management.
Ultimately, you’ll find that many modern systems, including group-sharing platforms like AccountShare, don’t force you into one box. They often use a hybrid approach—using RBAC as the bedrock for general permissions while layering on ABAC-style rules for more specific, context-aware security. This layered strategy often gives you the best of both worlds.
For a deeper look at how to implement these ideas effectively, check out our guide on the top access control best practices for 2025.
The Future of Access Management and Security

The world of access control is never static. The models we've explored—DAC, MAC, RBAC, and ABAC—are the bedrock of modern security, but the ground is already shifting. We're on a path away from rigid, one-time checks toward a future where security is smarter, more adaptive, and far less intrusive for the user.
This evolution isn't just a niche trend; it's a massive market transformation. The global access control market was recently valued at USD 10.76 billion and is expected to hit USD 11.56 billion shortly, growing at a rate of 8.4% through 2030. This growth is being fueled by companies adopting advanced tech like AI to stay ahead of increasingly sophisticated security threats. You can dive deeper into these market trends in a report by Grand View Research.
The Rise of Continuous Authentication
One of the biggest changes on the horizon is the shift to continuous authentication. Forget just checking a password at the door. New systems are being designed to constantly and subtly verify a user's identity in the background. It’s the difference between a bouncer who checks your ID once and a security guard who discreetly observes behavior throughout the night.
Think about what that means in practice. Future systems will analyze subtle, almost invisible patterns to confirm you are who you say you are.
- Behavioral Biometrics: How fast is your typing cadence? What are your unique mouse movement patterns?
- Contextual Cues: Are you logging in from your usual location and device? Is it a normal time of day for you to be working?
- Usage Patterns: Are you suddenly accessing files you've never touched before?
This data builds a living, breathing security profile for each user. If your behavior suddenly deviates from that baseline—even with the correct password—the system can flag it as a risk and demand extra proof of identity.
The core idea is to move from a single point-of-entry verification to a constant state of verification. This makes it much harder for an attacker with stolen credentials to cause damage because their behavior won't match the legitimate user's.
AI and Machine Learning in Security
Artificial intelligence and machine learning are the engines making this new era of security possible. They excel at finding the needle in the haystack—spotting tiny anomalies across vast datasets that a human administrator would almost certainly miss.
For instance, an AI-driven system can learn the typical access patterns for every single person in a company. If an employee who exclusively works with marketing documents suddenly attempts to download sensitive financial records at 3 AM, the AI can instantly block the action and notify the security team. This is a game-changer, moving security from a reactive stance (cleaning up after a breach) to a proactive one (stopping a breach before it ever happens).
This kind of intelligent automation is absolutely essential for securing today’s remote and hybrid work environments, where people connect from anywhere, on any device. Cloud-native access control, supercharged with AI, can adjust permissions on the fly based on real-time risk. Security no longer lives in the office; it follows the user, wherever they go. It's this forward-thinking approach that makes modern access control so critical for tackling the challenges ahead.
Your Access Control Questions, Answered
As you start digging into access control, a few practical questions always seem to pop up. It makes sense—choosing the right framework isn't just a theoretical exercise; it has real-world consequences for your security and workflow. Let's tackle some of the most common ones.
Can I Mix and Match Different Access Control Models?
Absolutely. In fact, creating a hybrid system is often the smartest approach. Many organizations use Role-Based Access Control (RBAC) as the backbone of their security, setting up standard permissions for different departments or teams. It’s clean and easy to manage for day-to-day operations.
But for high-stakes data or critical applications, they might layer Attribute-Based Access Control (ABAC) on top. This adds dynamic, context-sensitive rules for situations demanding stricter security. The trick is to design them carefully so the policies work together seamlessly, without accidentally creating blind spots or security loopholes.
What’s the “Principle of Least Privilege” All About?
The principle of least privilege (PoLP) is one of the cornerstones of modern cybersecurity. At its core, it’s a simple idea: a user should only have the bare minimum permissions required to do their job. Nothing more, nothing less.
Think of it like giving a valet a key that only starts the car and opens the driver's door—it won't open the trunk or the glove box. By enforcing PoLP through models like RBAC or ABAC, you dramatically shrink your attack surface. If an account is ever compromised, the damage is contained because the intruder can only access a very limited set of resources.
How Does “Zero Trust” Fit into All of This?
Zero Trust is a modern security philosophy that essentially flips the old "trust but verify" model on its head. It operates on the motto "never trust, always verify."
A Zero Trust security model treats every access request as if it's coming from an untrusted network. It doesn't matter if the user is in the office or at a coffee shop—they must be rigorously verified every single time before being granted access to anything.
Instead of granting broad access based on network location (like being inside the company firewall), Zero Trust relies heavily on sophisticated access control to constantly check who you are, what device you're on, and the context of your request before letting you in.
Ready to bring smart, secure access management to your shared subscriptions? With AccountShare, you can easily apply these principles to your group accounts. Ensure everyone gets the access they need—and nothing they don’t—all while saving money. Discover a better way to share your premium tools.
