
Top Access Control Software Solutions for Your Business
Share
At its heart, access control software is the brain of your building's security system. It's the central command that dictates who can go where—and when. Think of it as evolving far beyond simple keycard systems. Today's platforms are sophisticated enough to integrate with your entire business infrastructure, creating a smarter, more responsive security environment. This kind of software is no longer a "nice-to-have"; it's an essential tool for protecting assets, keeping people safe, and meeting compliance standards.
Understanding the Core of Modern Security

On a fundamental level, access control software is all about automating security policies. It replaces the old-school reliance on physical keys and manual guard checks with a digital database that grants or denies entry based on rules you define. This move from physical to digital completely changes how businesses handle security.
The demand for these advanced systems is exploding. The global access control market is expected to surge from USD 19.05 billion in 2025 to USD 61.31 billion by 2035. That’s not just growth; it's a massive shift, showing just how critical this technology has become across every industry.
From Keys to the Cloud: A Security Revolution
Looking back at the evolution of access control really puts its importance into perspective. What started with a single keycard reader on one door has blossomed into a fully connected ecosystem. A modern system lets you manage hundreds of doors across multiple sites, all from one dashboard.
The real power of today’s access control software is its ability to deliver fine-grained control and real-time visibility. It's not just about locking doors anymore. It’s about building an intelligent security bubble that can adapt on the fly to new threats and operational needs.
This transformation has been fueled by a few key technology shifts:
- Cloud-Based Platforms (ACaaS): Access Control as a Service (ACaaS) has been a game-changer. It enables remote management, pushes automatic software updates, and gets rid of the need for bulky on-site servers.
- Mobile Credentials: Smartphones are the new keys. This offers incredible convenience and lets administrators grant or revoke access in seconds, from anywhere.
- Biometric Integration: Technologies like fingerprint scanners and facial recognition add a much stronger layer of security by verifying who someone is, not just what credential they're holding.
- Deep Integration: The best systems today don't operate in a silo. They talk to video surveillance, alarm systems, and even HR software to create one unified security and operations hub.
Why the Software Is the Most Critical Piece
While hardware like locks and readers get all the attention, it's the software that holds all the intelligence. It’s the engine that processes every access request, logs every event for a perfect audit trail, and lets you build complex, layered security rules. For a deeper look at the nuts and bolts, our complete security roadmap breaks down how these pieces fit together.
Ultimately, without powerful software, even the most advanced hardware is just a box of parts. It’s the software that truly brings your building’s security potential to life.
Comparing the Top Access Control Software Platforms
Choosing the right access control software is a huge decision. It’s the brain behind your building's security, and the choice you make will echo through your daily operations, security posture, and even your ability to grow. The market is crowded with great options, but the "best" one is entirely dependent on what you actually need. Forget generic feature lists; we're going to break down the leading solutions by looking at what really matters in the real world: scalability, the day-to-day administrative experience, and how well the software plays with other systems.
This comparison is all about the nuances. One system might be a powerhouse built for a sprawling corporate campus with thousands of employees, while another is brilliantly simple, making it perfect for a small business or a multi-tenant apartment building. Let's dig in.
Differentiating by Scalability and User Management
One of the first questions you have to ask is, "Can this system grow with us?" A platform that feels great for a 50-person office can quickly become an administrative nightmare when you hit 500 employees spread across multiple sites.
For large enterprises, scalability is about more than just adding user slots. It’s about managing complex permission hierarchies, juggling multi-site access rules, and setting global policies without slowing the system to a crawl. The platforms built for this scale often run on a distributed architecture with beefy databases that can handle tens of thousands of access events every day.
On the other hand, a small or medium-sized business (SMB) needs simplicity above all else. Their ideal software lets an office manager—who is definitely not a full-time security pro—add a new hire, drop them into the "Marketing" group, and have their access rights instantly work on the right doors. It's all about efficiency.
The Expert Takeaway: Don't just ask if it can handle more users. The real question is, "How much more work will it be for my team as we scale?" A truly scalable system makes managing a complex organization feel simpler, not harder.
The Administrative Experience: Interface and Workflow
How the software feels to use every day is just as critical as its technical specs. A clunky, confusing interface is a recipe for mistakes, frustrated admins, and dangerous security gaps.
Scenario A: The Intuitive SMB Platform
Picture a coworking space manager needing to get five new members set up. A great SMB-focused platform gives them a clean, web-based dashboard where they can:
- Create new user profiles in less than a minute.
- Assign them all to a pre-set "Member" role with a single click.
- Instantly push mobile credentials to their smartphones.
The whole process is fast, intuitive, and requires almost no training. The design philosophy is speed and ease of use.
Scenario B: The Powerful Enterprise Console
Now, let's switch gears to a hospital security director managing a 2,000-bed facility. Their world is infinitely more complex. The software has to support incredibly granular, role-based access to protect sensitive areas like the pharmacy, operating rooms, and patient record data centers.
This is where a deep, feature-rich administrative console proves its worth. It might take longer to master, but it offers total control. The director can build sophisticated rules, like requiring two-factor authentication (a badge plus a PIN) for high-security zones, and pull detailed audit logs to prove compliance.
The chart below shows how different features are being adopted, highlighting the need for software that can handle both basic and advanced security functions.
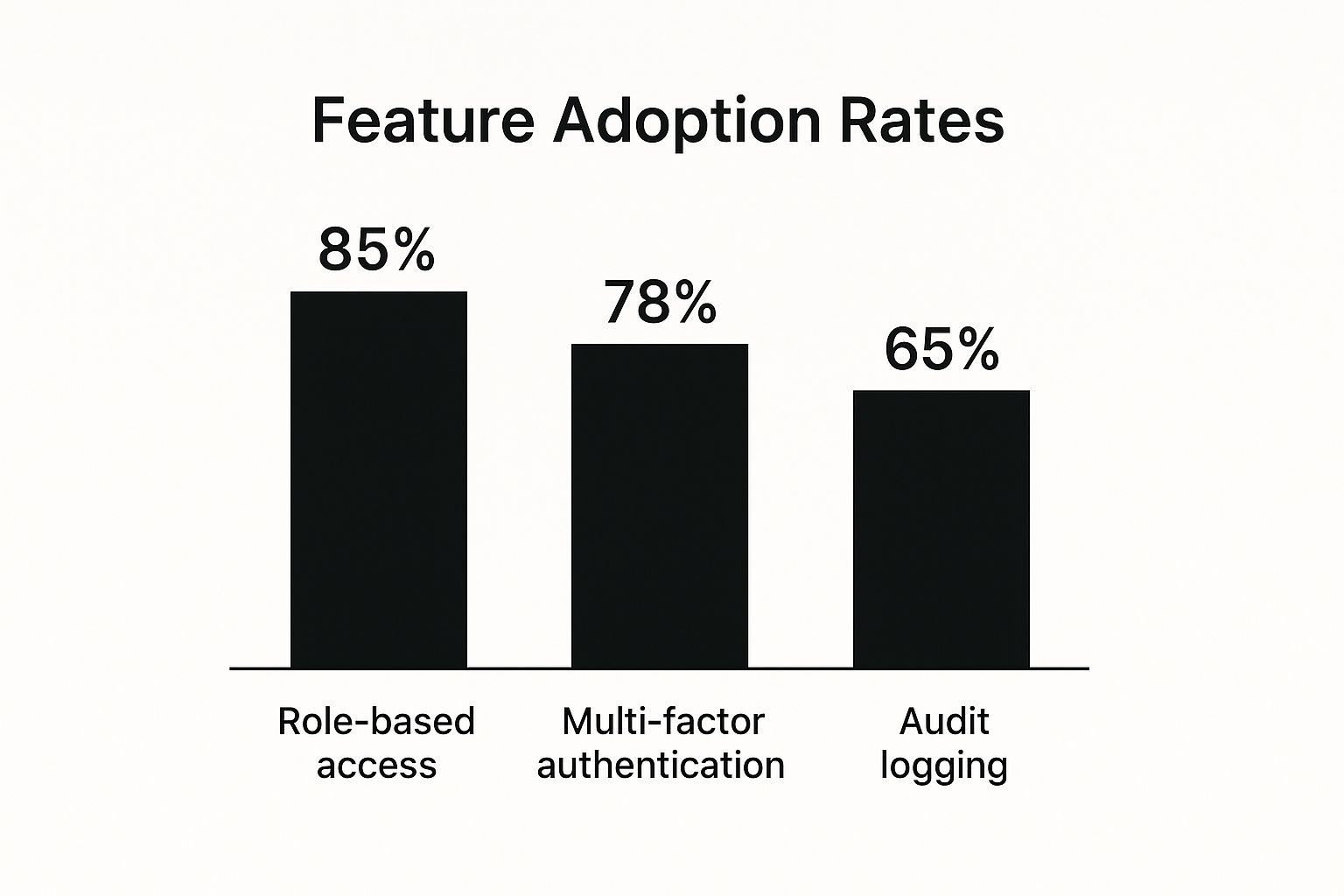
As you can see, while role-based access is a given, more robust measures like multi-factor authentication are becoming common. This trend shows why it's critical to have a platform that can manage this growing complexity without overwhelming your team.
To help you see how these platforms stack up at a glance, we've put together a high-level comparison of key features.
Feature Comparison of Leading Access Control Platforms
This table compares key functionalities across the top access control software, focusing on features critical for modern security management.
| Feature | Software A (Enterprise Focus) | Software B (SMB-Friendly) | Software C (Cloud-Native) | Software D (Legacy Hybrid) |
|---|---|---|---|---|
| Mobile Credentials | Advanced (NFC, BLE, Wallet) | Standard (App-based) | Native Wallet Integration | Optional Add-on |
| Visitor Management | Deep Integration | Basic Guest Passes | Fully Integrated & Automated | Separate Module |
| Video Integration | Extensive (VMS, AI) | Basic (Event-based clips) | Native Camera Support | VMS Integration |
| API & SDK Access | Full, Robust | Limited API | Open API Standard | Limited, Proprietary |
| Multi-Site Management | Global, Partitioned | Simple, Group-based | Centralized Cloud Dashboard | Federated Servers |
| Reporting & Auditing | Custom, Compliance-focused | Pre-canned Reports | Real-time Analytics | Standard Logs |
| Ideal User | Large Corp, Hospital | Small Office, Retail | Multi-site SMB, Coworking | Established Enterprise |
This table provides a snapshot, but remember that the devil is in the details of implementation and daily use. A feature that looks great on paper might be cumbersome in practice, which is why a hands-on demo is always a good idea.
Integration Capabilities: The Key to a Unified System
Modern security isn't an island. The most powerful access control software connects smoothly with your other business and security tools, creating a single, cohesive ecosystem.
Key integrations you should be looking for include:
- Video Surveillance: This is a big one. You want to link access events directly to video footage. For example, if a door is forced open, the system should automatically pull up the live feed from the nearest camera for instant verification.
- HR and Identity Management Systems: This automates the entire user lifecycle. A new hire is added to your HR platform, and an access profile is automatically created. When they leave, their credentials are just as quickly revoked everywhere.
- Visitor Management Platforms: This is all about streamlining the guest experience. An employee can pre-register a visitor, who then automatically receives a temporary mobile pass on their phone, valid only for specific doors and times.
This is a market that’s not just growing—it’s exploding. The global access control market is on track to jump from USD 13.72 billion in 2025 to over USD 39.24 billion by 2037. This massive growth is fueling major consolidation, like Honeywell's acquisition of Carrier Global’s Access Solutions business. These moves are a clear signal that the future is integrated, smarter systems. You can dive deeper into the forces shaping this market by checking out the latest access control market research.
Ultimately, picking the right platform comes down to honestly assessing your organization's real-world needs and finding the software whose strengths in scalability, administration, and integration are the best match for you.
Understanding Key Features and Core Technologies
To really compare access control software, you have to look past the brand names and get to grips with the technologies that make them tick. The right features aren't just about convenience—they're the very foundation of your security setup. Breaking down these components is the only way to make a smart decision that truly fits how your business operates.
The first big choice you'll face is how people will identify themselves. The type of credential you choose has a direct impact on security, how easy it is for your team to use, and what it'll cost you in the long run. Each method comes with its own trade-offs.
Comparing Modern Credential Types
The days of the simple magnetic stripe card are pretty much behind us. Modern systems give you a whole menu of options, from physical smart cards to digital credentials that live right on your smartphone.
- Smart Cards (RFID/NFC): These are a solid, familiar choice. The encrypted data on these cards makes them much more secure than older magstripe tech. The downside? They can still be lost, stolen, or passed around, which creates security gaps and replacement costs.
- Mobile Access Credentials: Turning a smartphone into a key is a game-changer for convenience. Admins can grant or revoke access remotely in an instant, which is perfect for managing a changing workforce or frequent visitors.
- Biometrics (Fingerprint/Facial Recognition): This is the top tier of security. Instead of verifying something a person has (like a card), it verifies who a person is. It completely eliminates the problem of shared or stolen credentials, but you have to be prepared for higher upfront hardware costs and navigate data privacy rules carefully.
The biggest shift I've seen in this space is the move toward mobile and biometric credentials. They finally solve the age-old problem of lost or shared keycards and give administrators a level of dynamic control that was unthinkable a decade ago.
Picking the right credential is all about balancing these factors. A high-security data center might make biometrics mandatory, while a trendy co-working space will likely prefer the flexibility of mobile access. For a deeper dive, check out our guide on different access control methods.
On-Premise vs. Cloud-Based Deployments
Another crucial decision is where your access control software actually lives. This choice has massive implications for your budget, future growth, and day-to-day system management.
On-Premise Systems
With an on-premise solution, all the software and data are stored on your own servers at your physical location. This gives you total control over your hardware and data, which is non-negotiable for some organizations with strict data sovereignty policies.
The catch is that this model demands a major upfront investment in servers and IT infrastructure. You're also on the hook for all maintenance, software updates, and security patches, which puts a heavy burden on your IT team.
Cloud-Based Systems (ACaaS)
Access Control as a Service (ACaaS) flips the script. The software is hosted in the cloud by a provider, and you simply access it through a web browser or mobile app. This subscription-based approach gets rid of the need for on-site servers, slashing your initial costs.
Even better, the provider handles all the backend work—maintenance, security, and updates—so your system is always up-to-date. This model is also incredibly scalable and makes managing multiple locations from a single dashboard a breeze.
| Feature Comparison | On-Premise Solution | Cloud-Based (ACaaS) |
|---|---|---|
| Initial Cost | High (servers, licenses) | Low (subscription fee) |
| Scalability | Limited by hardware | Virtually unlimited |
| Remote Access | Complex to configure securely | Native and secure |
| Maintenance | Managed by internal IT staff | Managed by the provider |
| Ideal For | Single-site, high-security facilities | Multi-site businesses, SMBs |
The Growing Role of AI and Machine Learning
The most forward-thinking access control software is now using Artificial Intelligence (AI) and Machine Learning (ML) to shift from reactive to proactive security. Instead of just recording events, these smart systems analyze access data to spot unusual behavior that could signal a threat.
For instance, an AI-powered system can flag an attempt to access a server room at 3 AM, even if the credential is valid. This gives security teams a chance to investigate a potential problem before it turns into a full-blown incident. This combination of AI and IoT is a huge factor in the industry's growth, with the access control market projected to expand from USD 11.06 billion in 2024 to USD 25.15 billion by 2034. AI-driven biometrics and behavioral analytics are leading the charge, offering a level of accuracy in threat detection we've never seen before.
Ultimately, getting a handle on these core technologies—credentials, deployment models, and smart analytics—is what lets you see past the marketing fluff. It helps you focus on the features that will actually deliver real security and operational value to your organization.
Choosing the Right Access Control for Your Business
Finding the right access control software isn't about chasing the "best" system on the market. It’s about matching the tool to the job. The security needs of a quiet suburban office are worlds away from those of a bustling, multi-story commercial building, and the software should reflect that reality.
When you move past generic feature lists and start thinking in terms of real-world scenarios, you can see exactly how a platform will solve your specific problems. Let’s walk through three common business environments and see how their unique demands point to very different access control solutions.
The Challenge: A Multi-Tenant Commercial Building
Imagine managing a high-rise filled with dozens of different companies. You have a constant stream of people—employees, clients, delivery drivers, and maintenance crews. Your goal is to keep the building secure without creating frustrating delays for everyone who has a legitimate reason to be there.
For this kind of environment, you absolutely need software with these capabilities:
- Partitioned Management: The building manager needs a master view, but each tenant company must have its own private portal to manage its employees. This is crucial for privacy and prevents one company from accidentally creating security gaps for another.
- Integrated Visitor Management: A clunky visitor sign-in sheet won’t cut it. The system should let tenants pre-register their guests, who then automatically receive a temporary mobile pass. This pass should only work for specific doors—like the main entrance and their host's floor—and expire after their meeting.
- Smart Elevator Control: An employee’s badge should only grant them access to their own company’s floor and any shared amenity spaces like a gym or cafeteria. This prevents people from wandering onto floors where they don’t belong.
A cloud-based access control software (ACaaS) built for multi-tenancy is the clear choice here. It gives the property manager centralized control while empowering individual tenants to handle their day-to-day access needs, solving a massive operational headache.
The Challenge: A Modern Hybrid Office
The hybrid work model created a new set of access challenges. Employees pop in and out on flexible schedules, making it tough to track who's on-site and manage credentials efficiently. The focus here shifts from rigid control to flexibility, automation, and a seamless user experience.
The golden rule for a hybrid office: if managing access for your flexible team feels like a full-time job, your system is broken. The software should do the heavy lifting for you.
For a hybrid setup, these features are non-negotiable:
- HR System Integration: This is a must-have. By connecting your access control to an HR platform like Workday or BambooHR, the entire process becomes automated. New hires get access on day one, and when someone leaves, their credentials are shut off instantly across all locations.
- Advanced Mobile Credentials: People live on their phones, and building access should be no different. The software needs to support easy-to-use mobile credentials, especially wallet-native passes that don't require fumbling with a separate app.
- Occupancy and Space Insights: You need data. The system should tell you who is in the office and when they’re there. This information is invaluable for everything from emergency headcounts to making smart decisions about your real estate footprint based on how the space is actually being used.
A cloud-native solution with an open API is the perfect fit for a hybrid office. It allows you to easily plug into your existing HR systems, room booking software, and other business tools to create a truly connected and automated workplace.
The Challenge: A High-Compliance Facility
Now think about a data center, a pharmaceutical lab, or a government facility. In these places, security isn’t just about keeping people out—it’s about proving who went where and when for strict audit and compliance purposes. Convenience takes a backseat to verifiable, layered security.
The software for this environment must deliver on:
- Multi-Factor Authentication (MFA): A simple card swipe isn't enough for high-security areas. The system has to enforce policies that demand a credential plus a second factor, like a PIN code, a biometric scan (fingerprint or face), or a mobile authenticator app.
- Granular, Role-Based Access: You need surgical precision. Administrators must be able to create hyper-specific access rules. For instance, a network technician might only be allowed into a specific server row during their assigned 8-hour shift, and only after an approved work ticket has been submitted.
- Immutable Audit Trails: Every single event—a door unlocked, a permission changed, an alarm triggered—must be logged in a tamper-proof record. The software has to generate detailed, compliance-ready reports that can be pulled instantly for regulatory audits.
For these high-stakes use cases, an on-premise or private cloud deployment is often the right call to maintain absolute control over the data. The access control software chosen must have certified integrations with biometric hardware and feature a powerful, customizable reporting engine designed to meet the toughest compliance standards.
Analyzing Implementation Steps and Total Cost

Choosing a new access control software is about more than just features on a spec sheet. You have to get real about the money and the work involved. Understanding the true total cost of ownership (TCO) and having a clear implementation plan is what separates a smooth rollout from a surprise budget nightmare. Let's walk through the whole process, from the initial check you write to the long-term value you get.
Your first major financial hurdle is deciding between two very different pricing philosophies. Each one shapes your budget in a fundamental way, both today and for years to come.
Perpetual License vs. SaaS Subscription
With a perpetual license, you make a large, one-time payment to own the software forever. It's a significant upfront hit to your capital budget, no doubt. But over the long haul—say, five to ten years—it can lead to a lower TCO because you're not paying recurring fees for the core platform.
The alternative is the Software as a Service (SaaS) model, which has become the standard for most cloud-based systems. Here, you pay a predictable monthly or annual subscription. This approach makes powerful access control software much more accessible, as you don't need a massive initial investment. Plus, the fee typically bundles in support, maintenance, and all the latest updates, rolling your operational costs into one clear number.
The choice between perpetual and SaaS is a strategic financial decision. A perpetual license front-loads the cost for long-term ownership, while SaaS spreads it out, turning a capital expense into a predictable operational expense.
Breaking Down the Total Cost of Ownership
That initial license or subscription fee? It’s just the beginning. A realistic budget must account for all the other expenses that make up the true TCO.
- Hardware Costs: This is the physical stuff—the readers, controllers, locks, and maybe even new servers if you're keeping everything on-premise.
- Installation Fees: Getting a professional to install everything correctly is non-negotiable for system reliability. The cost can swing wildly depending on how complex your facility is and how many doors you’re securing.
- User Training: Your team needs to know how to drive the system. Setting aside a budget to train administrators and get employees comfortable with the new process is absolutely vital for making it stick.
- Ongoing Maintenance: For on-premise systems, you need to plan for potential hardware failures and the IT staff time to manage it all. With SaaS, this is usually baked into your subscription.
I've seen it time and again: failing to budget for these "hidden" costs is one of the quickest ways to derail an access control project.
The Implementation Project Roadmap
A successful deployment isn't a race; it's a methodical, multi-stage process. Trying to cut corners here will only lead to security gaps and operational headaches later.
1. Site Assessment and System Design
This is the foundation. It starts with a detailed walkthrough of your building to identify every access point, figure out the right security level for each zone, and map out where all the hardware will go. This is where your system's blueprint is born.
2. Hardware Installation and Configuration
Next, certified technicians come in to install the physical gear—the card readers, door controllers, and all the wiring. At the same time, your IT team or the provider gets the access control software itself up and running, either on a local server or in the cloud.
3. User Onboarding and Training
With the system live, the focus shifts from technology to people. You’ll be importing user data, assigning initial access permissions, and training your admins on how to manage the platform. For a smoother transition, it's smart to review top access control best practices for 2025 to help shape your user policies from day one.
4. Post-Launch Support and Optimization
Once you go live, ongoing support is critical for squashing any bugs that pop up. This phase is also your chance to watch how the system is performing, get feedback from users, and fine-tune your access rules for the perfect balance of security and convenience.
By carefully planning for both the financial investment and the step-by-step implementation, you can make sure the solution you pick is not only powerful but also becomes a seamless and successful part of your organization.
Answering Your Top Access Control Software Questions
Diving into physical security systems can feel overwhelming, and it's natural to have questions when you're trying to pick the right technology. Let's break down some of the most common things people ask about access control software. Getting these answers straight will help you make a much more confident choice.
A huge point of discussion always comes down to where the system is managed: on your own servers or in the cloud. This decision has major security implications.
Is Cloud-Based Access Control Really More Secure Than On-Premise?
This isn't a simple yes-or-no question. It's about weighing two very different approaches to security.
With an on-premise system, you have direct, physical control over the server. For some, that feels inherently safer. But that control comes with a heavy burden—you are 100% responsible for every single security patch, update, and physical defense against tampering. It's all on your team.
Cloud-based access control software, often called ACaaS (Access Control as a Service), flips that model. You're handing off the server management to a specialized provider who lives and breathes security. These companies, like Amazon Web Services or Microsoft Azure, spend billions on security infrastructure, round-the-clock monitoring, and data encryption. They handle all the patches and updates behind the scenes, so your system is never vulnerable because someone forgot to run an update.
The real question to ask is: who is better equipped to protect a complex system that's connected to the internet? For most businesses, a dedicated cloud provider's security team will offer a stronger defense than an internal IT department that has to juggle dozens of other priorities.
While a meticulously managed on-premise system can be quite secure, a cloud platform almost always gives you a higher level of security and reliability right out of the box.
What Are the Must-Have Integrations for an Access Control System?
An access control system that stands alone is a missed opportunity. Its real value shines when it communicates with your other critical business systems, turning simple security events into useful, actionable information. From my experience, three integrations are absolutely essential for elevating both your security and day-to-day operations.
- Video Surveillance Systems: This is the most fundamental link. Tying access events to video footage gives you immediate context. When a door is forced open, you shouldn't just get an alert; you should instantly see the live camera feed from that exact location.
- HR Information Systems (HRIS): This integration is a lifesaver for automating employee access. A new hire is entered into the HR system, and their access credentials are created automatically. Even more critically, when an employee leaves the company, their access is instantly and automatically revoked, plugging what is often a huge security hole.
- Visitor Management Platforms: If your facility has a steady stream of guests, this is non-negotiable. It lets your team pre-register visitors, who then get a temporary mobile pass that only works in designated areas and for a specific time. It’s a smooth, professional, and secure way to manage non-employee access.
These connections are what change your access control software from a basic lock-and-key system into the intelligent core of your building's security.
Can I Keep My Old Hardware and Just Upgrade the Software?
This is a very common question, especially from organizations trying to modernize without a huge upfront investment. The short answer is: maybe. It really depends on the age and type of your existing hardware.
Many modern software providers have developed universal controllers or gateway devices specifically designed to communicate with older-generation card readers and electric locks. This can be a viable path.
But you have to weigh the trade-offs carefully. Older hardware might not support the robust encryption standards of today, potentially creating a weak link in your security chain. What's more, trying to make old equipment and new software play nice can lead to a never-ending cycle of troubleshooting and technical support calls. It can become a real headache.
In many situations, opting for a complete hardware replacement, while more expensive at the start, ends up being the more secure, reliable, and ultimately more cost-effective choice over the long haul.
Ready to simplify your digital life without breaking the bank? With AccountShare, you can get access to premium software and subscriptions at a fraction of the cost. Join a group and start enjoying the benefits of shared access today. Learn more about sharing accounts.
