
6 Smart Safe Way to Share Passwords in 2025
Share
Unlocking Secure Password Sharing: Your 2025 Guide
Sharing access to streaming services, AI tools, or collaborative software is often necessary, but finding a truly safe way to share passwords is critical. This guide cuts straight to the chase, detailing practical methods to protect your sensitive credentials. Discover how encrypted password managers, secure messaging with disappearing messages, PGP/GPG email encryption, secure file sharing services, air-gapped techniques, and even encrypted QR codes can safeguard your information. Mastering these strategies is essential for secure collaboration and account management in 2025, keeping your digital life protected.
1. Encrypted Password Managers
Encrypted password managers are a cornerstone of modern digital security, providing a robust and safe way to share passwords while managing numerous login credentials. These applications function as secure digital vaults that store, generate, and autofill passwords. Their security relies on strong end-to-end encryption (typically AES-256), scrambling your data before it leaves your device. The entire vault is protected by one strong master password – the only one you need to remember.

Password managers are essential because data breaches and password reuse are rampant vulnerabilities. They offer a critical defense for individuals managing many logins, families sharing account access (e.g., streaming services), and businesses needing a safe way to share passwords for team collaboration. By enabling controlled, encrypted sharing, they eliminate risky habits like emailing passwords or writing them down. This is vital for granting temporary or specific access without exposing actual credentials, thus offering a truly secure method for password sharing.
The strength of encrypted password managers lies in their key features:
- End-to-end AES-256 Encryption: Often called military-grade, this encrypts your data on your device before cloud sync (if any) and decrypts it only locally with your master password. Service providers cannot access your stored passwords.
- Zero-Knowledge Architecture: This principle ensures the service provider has no knowledge of your master password or your encrypted data. All encryption and decryption happen locally, enhancing trust and privacy.
- Automatic Password Generation: Creates long, complex, unique passwords for each account, eliminating weak or reused passwords and significantly boosting security.
- Cross-Platform Synchronization: Offers apps and browser extensions for major operating systems and browsers, ensuring seamless password access across all your devices.
- Secure Sharing with Granular Permissions: This is crucial for a safe way to share passwords. You can share specific credentials with individuals or teams, controlling view/use permissions, setting time limits, and revoking access instantly.
- Two-Factor Authentication (2FA) Support: Adds an extra security layer to your password manager account itself, requiring a second verification form beyond the master password.
- Password Strength Analysis: Audits your stored passwords, flagging weak, reused, or potentially compromised ones, and prompting updates.
The advantages of adopting an encrypted password manager are significant:
- Top-Tier Security: Military-grade encryption and zero-knowledge architecture protect your data.
- Simplified Management: Remember only one master password; the manager handles the rest.
- Time-Saving: Autofill and one-click logins streamline online access.
- Instant Access Revocation: Critical for security when sharing access with employees or family.
- Audit Trails: Tracks shared password access, enhancing accountability, especially for businesses.
- Universal Accessibility: Works across devices and browsers for consistent access.
However, consider these potential drawbacks:
- Master Password Vulnerability: If your master password is compromised, your entire vault is at risk. Its strength and secrecy are paramount.
- Provider Trust: You entrust your encrypted data to a third party. Choose reputable providers with strong security records.
- Subscription Costs: Many top services have recurring fees, though some, like Bitwarden, offer strong free tiers.
- Learning Curve: Non-technical users might need time to learn all features, though most are user-friendly.
- Hacker Target: Centralized data can attract hackers, but robust encryption is designed to defend against this.
The effectiveness of password managers is clear from their widespread adoption. 1Password serves over 100,000 businesses, including Slack and GitLab. Open-source Bitwarden is used by large firms like IBM. LastPass is popular among families for sharing, and Dashlane helps startups manage team credentials. These examples show password managers provide a reliable and safe way to share passwords for diverse users, from students looking for affordable options to digital nomads needing efficient account management.
To maximize security and utility:
- Use a Strong Master Password with 2FA: Make it long (at least 16 characters), unique, complex (mix of cases, numbers, symbols), and crucially, enable Two-Factor Authentication (2FA) on your password manager account.
- Audit Shared Access Regularly: Periodically review and remove unnecessary access to shared credentials for former employees or changed project roles.
- Set Up Emergency Access: Allow a trusted contact (e.g., spouse, family member) to request vault access in emergencies, after careful configuration.
- Enable Breach Monitoring: Utilize built-in services that alert you if your credentials appear in known data breaches, so you can change them immediately.
- Organize with Shared Folders: For teams or families, use shared folders (or collections/vaults) to logically group credentials by project, department, or service type. This simplifies permission management for a safe way to share passwords with relevant groups.
Encrypted password managers are a leading safe way to share passwords, benefiting tech-savvy users, families wanting to share streaming accounts, small businesses needing collaborative tools, and many others. Their blend of robust security, user-friendliness, and controlled sharing makes them vital digital tools. By centralizing and encrypting credentials, they simplify online life and significantly boost security. Learn more about Encrypted Password Managers and further best practices for digital security.
2. Secure Messaging Apps with Disappearing Messages
In an age where digital privacy is paramount, finding a truly safe way to share passwords and other sensitive information can be challenging. One increasingly popular and effective method leverages the technology already in many people's pockets: secure messaging apps equipped with disappearing or self-destructing message features. This approach combines robust end-to-end encryption with the ephemeral nature of temporary messages, creating a secure channel that significantly minimizes the risk of password exposure. Essentially, you're sending sensitive data through a tunnel that not only protects it during transit but also ensures the message itself vanishes after a short, predefined period.

The core principle behind this method is straightforward. You and the recipient use a messaging application that offers end-to-end encryption (E2EE). This means that from the moment you send the message until the recipient opens it, the content is scrambled and unreadable to anyone else – including the app developers themselves. Many top-tier secure messaging apps, like Signal (whose protocol was pioneered by Moxie Marlinspike), utilize the highly regarded Signal Protocol for their E2EE. The "disappearing messages" feature adds another crucial layer: you can set a timer for how long the message (containing the password) remains visible to the recipient. Once this timer expires, the message automatically deletes itself from both your device and the recipient's device, leaving no readily accessible digital trace in the conversation history.
This combination makes it a compelling safe way to share passwords for specific scenarios. For families wanting to temporarily share a streaming service login, or a small business needing to give a contractor short-term access to a tool, this method offers a balance of security and convenience without resorting to less secure options like plain text emails or standard SMS.
Key Features and Their Security Significance
Understanding the features of these apps highlights why they are a recommended solution:
- End-to-End Encryption (E2EE): As mentioned, this is foundational. Only the sender and the intended recipient possess the keys to decrypt and read the messages. This protects the password from interception during transit over Wi-Fi or mobile networks.
- Self-Destructing Messages: This is the star feature for password sharing. By setting a short timer (e.g., 5-10 minutes), you ensure the password isn't lingering in chat logs, vulnerable to later device compromises or unauthorized access.
- Screenshot Detection and Blocking: Some apps (like Signal and Telegram's Secret Chats) attempt to notify you if the other person takes a screenshot or try to block screenshots altogether. While not foolproof (e.g., someone could use another device to photograph the screen), it acts as a deterrent and an awareness tool.
- No Cloud Storage of Messages (for encrypted content): While apps might back up general settings, end-to-end encrypted messages with disappearing timers are typically not stored decrypted on any cloud server. They exist primarily on the users' devices for the duration they are visible.
- Forward Secrecy (or Perfect Forward Secrecy - PFS): This advanced cryptographic feature ensures that even if a long-term secret key is compromised in the future, past messages (like a shared password) remain secure because each session uses unique, temporary keys.
- Verification of Contact Identity: Most secure apps provide ways to verify that you're communicating with the correct person, often through safety numbers or QR codes that can be compared in person or through another secure channel. This helps prevent man-in-the-middle attacks.
- Cross-Platform Availability: Apps like Signal, WhatsApp, and Telegram are available on iOS, Android, and often desktop, making them accessible to a wide range of users.
Pros: The Upsides of Ephemeral Sharing
- No Permanent Digital Trace: The primary advantage. The password vanishes, reducing the risk of future discovery.
- Strong Encryption: Industry-standard E2EE prevents unauthorized interception.
- Free to Use: Most of these secure messaging apps are free, making this a cost-effective option for everyone, from students to small businesses.
- Quick and Convenient: Ideal for urgent, on-the-fly sharing without complex setups. Digital nomads needing to quickly share a Wi-Fi password with a colleague can benefit greatly.
- No Third-Party Data Storage (of the sensitive message): You're not relying on a password manager's cloud or another third party to store this specific instance of the shared password long-term.
- Built-in Security Notifications: Apps often notify users of security-related events, like a contact's security code changing.
Cons: Potential Pitfalls and Limitations
- Requires Both Parties to Have the Same App: This can be a logistical hurdle if the recipient doesn't already use a compatible secure messenger.
- No Backup or Recovery: If the recipient misses the message before it disappears, or if they forget the password, it's gone. This is by design for security but can be inconvenient.
- Risk of Shoulder Surfing: The password is still visible on the recipient's screen when they view it. Physical security (ensuring no one is looking over their shoulder) remains crucial.
- Temporary Nature May Cause Confusion: If the recipient isn't expecting a disappearing message or doesn't see it in time, it can lead to missed information. Clear communication is essential.
- Limited to One-Time Sharing Scenarios: This method isn't a replacement for a robust password management strategy. It's best for ad-hoc, temporary sharing.
Examples in Action
- Signal: Widely trusted by journalists, activists, and security professionals for its strong privacy stance and robust E2EE. Ideal for highly sensitive communications.
- WhatsApp Disappearing Messages: A feature added to the world's most popular messaging app, making it accessible for casual users and small businesses to share temporary client credentials or Wi-Fi passwords.
- Telegram Secret Chats: Telegram, founded by Pavel Durov, offers "Secret Chats" which are end-to-end encrypted and support self-destruct timers, often used by remote teams for temporary access sharing.
- Wire: Another secure messaging platform, popular with government agencies and enterprises, that emphasizes security and offers ephemeral messaging.
Actionable Tips for Maximizing Security
To make this safe way to share passwords even safer:
- Set the Shortest Practical Timer: A 5-10 minute timer is often sufficient for the recipient to view and use the password. The shorter the exposure, the better.
- Verify Recipient's Identity: Before sending, confirm you have the right contact. Use the app's built-in contact verification feature or confirm through an out-of-band method (like a quick voice call).
- Confirm Receipt Immediately: Ask the recipient to acknowledge they've seen and noted the password before it disappears.
- Combine with Voice Call (Optional): For very sensitive passwords, initiate a voice call to verbally confirm they are ready to receive it and to verify their identity in real-time.
- Recipient Responsibility: No Screenshots or Copying: Advise the recipient to manually type the password where needed and not to screenshot it or copy it to their clipboard, as this can create new vulnerabilities.
- Change Password After Sharing (If Possible): If the password grants access to an important account, and it’s feasible, change the password after the recipient has used it for the intended one-time purpose. This is the gold standard for temporary access.
Secure messaging apps with disappearing messages offer a pragmatic and significantly safer alternative to insecure methods like email or SMS for sharing passwords in specific, limited contexts. While not a panacea for all password security challenges, they provide a valuable tool for tech-savvy individuals, families, and even small businesses looking for a quick, encrypted, and ephemeral safe way to share passwords without leaving a lasting digital footprint.
3. Encrypted Email with PGP/GPG
For individuals and organizations prioritizing robust, user-controlled security, leveraging encrypted email with Pretty Good Privacy (PGP) or its open-source counterpart, GNU Privacy Guard (GPG), stands as a formidable method. This approach offers an exceptionally safe way to share passwords and other sensitive information by employing powerful end-to-end encryption. Originally developed by Phil Zimmermann in 1991, PGP, and later GnuPG (created by Werner Koch), established a gold standard for secure digital communication by putting cryptographic tools directly into the hands of users.
At its core, PGP/GPG utilizes public-key cryptography. This ingenious system involves two distinct but mathematically linked keys for each user: a public key and a private key. The public key can be shared openly with anyone, like a secure mailbox slot. Conversely, the private key must be kept absolutely secret by its owner, acting as the unique key to unlock that mailbox. When you want to share a password securely with someone using PGP/GPG, you encrypt the email message containing the password using their public key. Once encrypted, the message becomes unreadable gibberish to anyone intercepting it. Only the intended recipient, possessing the corresponding private key, can decrypt and read the original password. This ensures that even if the email is intercepted during transit, the password remains confidential.
The strength of PGP/GPG lies in its mathematically proven encryption algorithms and its open-source nature (in the case of GnuPG), which allows for community vetting and transparency. Key features include not only strong encryption but also digital signatures. A digital signature, created using your private key, allows the recipient to verify that the message genuinely came from you and hasn't been tampered with—a crucial aspect when sharing critical access credentials. Furthermore, PGP/GPG is cross-platform compatible, works with virtually any email provider, and because users manage their own keys, it offers complete control and operates in a decentralized manner, meaning there's no single point of failure. Many modern email clients, such as Thunderbird (with OpenPGP integration) or dedicated services like ProtonMail, offer built-in or integrated PGP/GPG support, simplifying its adoption.
The fundamental process of sending an encrypted email with PGP/GPG involves a few key stages once the initial setup is complete. First, both sender and recipient must generate their own key pairs. The sender then needs the recipient's public key to encrypt the message. The recipient uses their private key to decrypt it. The following infographic visualizes this core three-step process of secure email encryption using PGP/GPG:
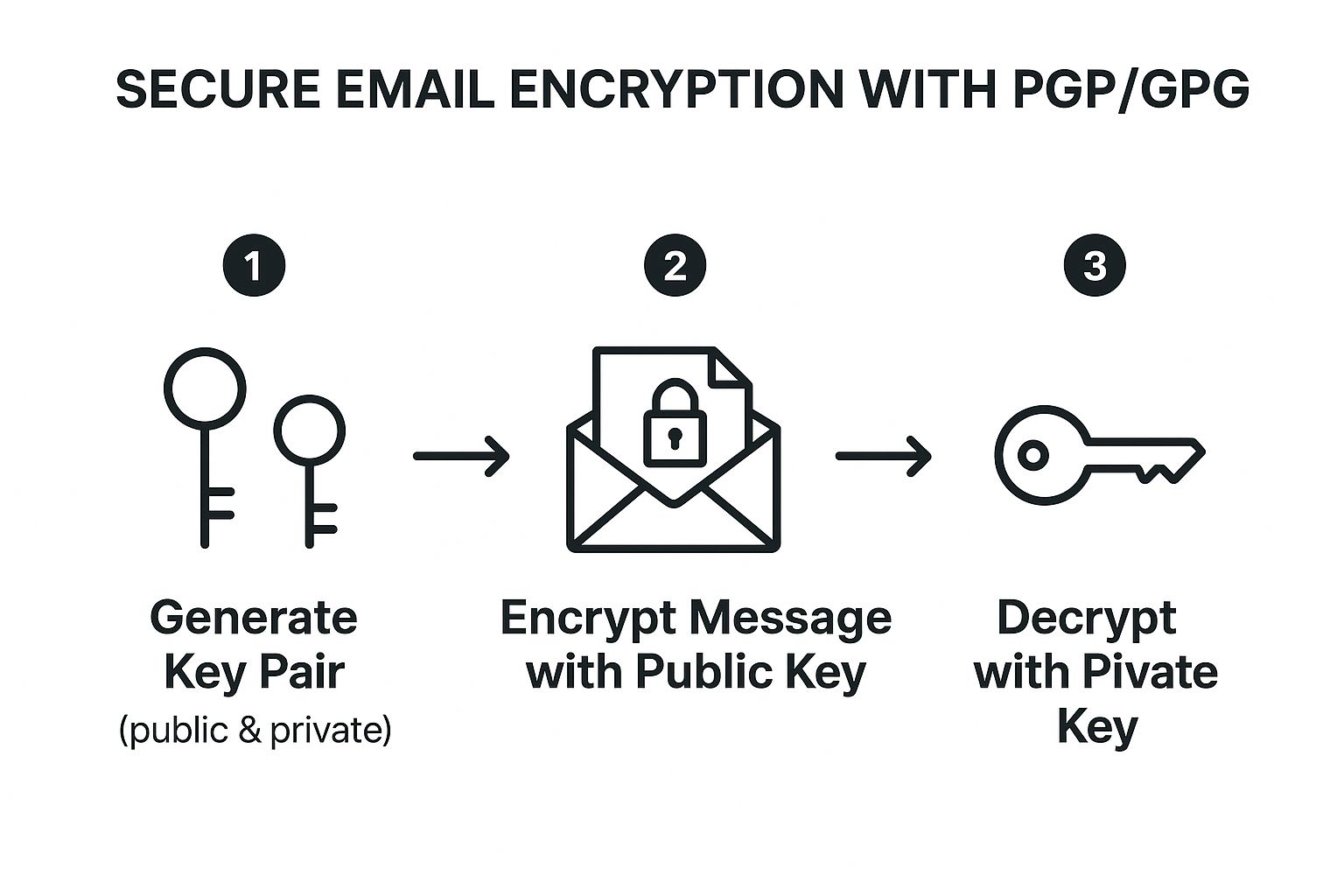
This flow highlights the fundamental asymmetry of public-key cryptography, where encryption and decryption are tied to distinct but mathematically linked keys, ensuring only the intended recipient can access the shared password.
Despite its undeniable security benefits, PGP/GPG is not without its challenges. The primary hurdle is its complexity; the setup process and ongoing key management can be daunting, presenting a steep learning curve for average, non-technical users. Securely exchanging public keys (key distribution) is another critical step that can be tricky; users must verify the authenticity of public keys, often via "key fingerprint verification" through a separate, secure channel, to avoid man-in-the-middle attacks. It's also important to note that PGP/GPG typically encrypts only the body of the email, leaving metadata like the sender, recipient, and subject line unencrypted (though services like ProtonMail may offer additional protections for this). Finally, the risk of losing or corrupting your private key is significant; if the private key is lost, any data encrypted with the corresponding public key becomes permanently inaccessible.
So, when and why should you choose PGP/GPG for sharing passwords? This method is best suited for situations where the utmost security and personal control are paramount, and the users involved are technically capable or willing to learn. It's an excellent choice for sharing highly sensitive information like master passwords, critical server credentials, or any data where a breach would have severe consequences. Tech-savvy individuals, journalists receiving sensitive information from sources (as advocated by organizations like the Electronic Frontier Foundation), software developers securing project communications, and privacy-conscious users often rely on PGP/GPG.
Examples of its successful implementation are widespread. ProtonMail and Tutanota have built entire secure email services around PGP/GPG principles, making end-to-end encryption more accessible. Journalists frequently use GPG to protect their sources when receiving sensitive credentials or documents. Software development teams often use GnuPG to sign code releases and communicate securely.
If you decide PGP/GPG is the right safe way to share passwords for your needs, follow these actionable tips:
- Generate Strong Key Pairs: Use at least 2048-bit RSA keys, or consider modern elliptic curve cryptography (ECC) for comparable security with smaller key sizes.
- Verify Key Fingerprints: Always verify the recipient's public key fingerprint through a trusted, out-of-band channel (e.g., phone call, in-person meeting) before encrypting sensitive data.
- Protect Your Private Key: Keep your private key offline if possible (e.g., on a USB drive), create secure backups, and protect it with a very strong passphrase.
- Use Email Clients with PGP Support: Consider clients like Thunderbird with OpenPGP, or tools like GPG Suite (macOS) or Kleopatra (Windows/Linux) to manage keys and encryption.
- Regularly Update and Consider Key Rotation: Keep your GPG software updated. While key rotation isn't always necessary for individuals, organizations might have policies for it.
In conclusion, while PGP/GPG demands a higher technical proficiency than many other password sharing methods, its robust, user-controlled, and time-tested encryption offers unparalleled security for those who need it, solidifying its place as a powerful option for protecting your most sensitive credentials.
4. Secure File Sharing Services
When the crucial task of sharing passwords or other highly sensitive information arises, especially within professional teams, with clients, or even among tech-savvy family members, the method of transmission is paramount. Simply attaching a password list to an email or sending it via a standard messaging app can expose it to significant risks. Secure File Sharing Services emerge as a robust and professional solution, offering a highly safe way to share passwords and other confidential data. These are cloud-based platforms meticulously engineered with enterprise-grade security features, specifically designed to protect your most sensitive information from unauthorized access during transmission, while in use, and at rest.
What Are They and How Do They Work?
Secure File Sharing Services are specialized cloud storage and collaboration platforms that prioritize security, control, and confidentiality for any digital asset, including documents that might contain passwords. Unlike general-purpose cloud storage, their architecture is fundamentally built around protecting sensitive information. The core mechanics generally involve:
- Client-Side Encryption (Often Zero-Knowledge): This is a critical feature for a safe way to share passwords. Before your file (e.g., an encrypted document, a secure note, or a password-protected spreadsheet) is uploaded, many leading services encrypt it directly on your device. This "zero-knowledge" encryption means that the service provider itself cannot decrypt or access the content of your files. Only you, and the recipients you authorize, possess the keys to unlock the information.
- Secure Upload and Storage: The already-encrypted file is transmitted to the service's servers over encrypted connections (e.g., HTTPS with TLS). Once on their servers, the files remain encrypted, often with an additional layer of server-side encryption.
-
Controlled and Auditable Sharing: When you're ready to share, you don't just send the file; you generate a secure, shareable link. These services provide a suite of controls to manage this link:
- Link Password Protection: You can (and should) add a separate password to the share link itself. This password should be communicated to the recipient via a different secure channel (e.g., a phone call or an end-to-end encrypted messaging app).
- Expiration Dates: You can set a specific date and time after which the link automatically becomes invalid, thereby minimizing the window of potential exposure for the shared passwords.
- Download Limits: You can restrict the number of times a file can be downloaded via the shared link.
- Recipient Authentication: Some advanced services may require recipients to verify their identity, perhaps by logging into an account on the platform, before they can access the shared file.
- Comprehensive Audit Trails: These platforms meticulously log all activities related to your files. This includes who uploaded a file, who accessed it, when they accessed it, their IP address, and what actions (e.g., view, download) they performed. These logs are indispensable for security monitoring, accountability, and meeting compliance requirements.
These combined features ensure that using such a service is a genuinely safe way to share passwords, especially when compared to less secure, conventional methods. If you're exploring options and want to compare different platforms, you can Learn more about Secure File Sharing Services to find one that fits your specific needs.
Why This Method Deserves Its Place: Key Features & Benefits
Secure File Sharing Services distinguish themselves through a comprehensive security posture, making them a prime choice for handling sensitive credentials:
- Uncompromising Encryption: The emphasis on client-side and zero-knowledge encryption is paramount. This ensures that even if the service provider's infrastructure were compromised, your actual password files would remain unreadable, a key characteristic of a safe way to share passwords.
- Granular Access Controls & Permissions: You maintain fine-grained control over who can access, view, edit, or download any shared password file. Permissions can often be customized on a per-user or per-group basis and, critically, can be revoked instantly.
- Professional Audit Trails for Compliance and Accountability: For businesses, especially those operating in regulated industries (like finance or healthcare), detailed and immutable access logs are not just a convenient feature but a stringent requirement for standards like SOC 2, HIPAA, or GDPR. These logs provide an essential layer of accountability.
- User-Friendliness and Workflow Integration: Many of these services are accessible via a web browser or dedicated apps, requiring minimal to no complex software installation. They often offer integrations with other business tools, streamlining secure practices into existing workflows.
- Scalability: Whether you're an individual needing to share a Wi-Fi password securely with a guest, a small business collaborating on project credentials, or a large enterprise managing access for hundreds of employees, these services can typically scale to meet varying demands.
- Industry Certifications: Reputable services often undergo rigorous third-party audits and achieve certifications against international security standards (e.g., ISO 27001, SOC 2 Type II), offering an independent validation of their security claims.
Real-World Implementations Demonstrating Success:
The practical value and robust security of these platforms are highlighted by their adoption across diverse and demanding sectors:
- SpiderOak, known for its strong cryptographic foundations, is frequently used by law firms for the secure exchange of highly confidential client credentials and sensitive case documents.
- Tresorit has found significant adoption in healthcare organizations. Its end-to-end encryption and detailed access controls are vital for sharing patient data or internal administrative passwords while adhering to stringent HIPAA compliance.
- Financial advisors and institutions often turn to services like pCloud Crypto for the secure transmission of client financial statements, investment details, and other sensitive personal identifiable information.
- Government contractors and agencies handling classified or "sensitive but unclassified" (SBU) information may utilize platforms like Sync.com, which are built with a strong emphasis on user privacy and robust data protection.
Pros:
- Typically accessible via web browsers, minimizing the need for software installation.
- Offers highly granular control over file access and user permissions.
- Provides detailed and professional audit trails, essential for compliance and security oversight.
- Can often integrate seamlessly with existing business applications and workflows.
- Scalable to support individuals, families sharing accounts, small businesses, and large enterprises.
- Encryption processes are largely automated, reducing the risk of human error in securing files.
Cons:
- Advanced features, higher storage capacities, and enterprise-level controls usually require a paid subscription.
- Access to files and sharing capabilities are dependent on a stable internet connection.
- A degree of trust in the service provider's security practices and infrastructure is necessary (though significantly mitigated by zero-knowledge architecture).
- There's a potential for accidental oversharing if users misconfigure sharing settings, emphasizing the need for careful use.
- Free or basic tiers may come with restrictive limitations on storage space or essential security features.
- While many services meet broad regulatory standards, they might not fulfill every specific or niche compliance requirement without additional configurations or attestations.
Actionable Tips for Maximizing Security When Sharing Passwords:
To ensure you are leveraging these platforms as the truly safe way to share passwords they are designed to be, consider these best practices:
- Always Set Strict Expiration Dates: For any file containing passwords or other time-sensitive credentials, limit its availability. Once the intended recipient has securely retrieved the information, the share link should expire.
- Enforce Link Passwords: Add an additional, strong password to the shared link itself. Crucially, communicate this password to the recipient through a completely separate and secure channel (e.g., an end-to-end encrypted call or message).
- Regularly Review and Audit Access Logs: Make it a routine to check the access logs for your shared password files. Investigate any suspicious or unrecognized activity immediately.
- Implement Two-Factor Authentication (2FA/MFA) for Your Account: Protect your own account on the secure file sharing service with 2FA. This adds a critical security layer, preventing unauthorized access even if your primary account password becomes compromised.
- Prioritize Services with Zero-Knowledge Encryption: Opt for platforms where you, and only you (along with your explicitly authorized recipients), control the decryption keys. This ensures the provider cannot access your sensitive data.
- Verify Recipient Identity Before Sharing: Especially for highly sensitive credentials, confirm the identity of the recipient through an out-of-band method (e.g., a quick video call or a pre-established secure phrase) before sending the share link.
By diligently applying these tips, Secure File Sharing Services stand as an exceptionally reliable and demonstrably safe way to share passwords. They offer a significant upgrade from insecure traditional methods, providing businesses and individuals alike with the necessary control, visibility, and robust cryptographic protection for their most vital credentials.
5. Physical Air-Gapped Methods
When considering a truly safe way to share passwords, especially for credentials guarding your most sensitive information, it’s crucial to explore methods that go beyond typical digital solutions. Physical Air-Gapped Methods represent an 'old-school' yet remarkably effective approach, completely sidestepping the risks inherent in online transmission and offering a robust layer of security for specific, high-stakes situations.
What are Physical Air-Gapped Methods and How Do They Work?
The term 'air-gapped' signifies complete isolation from any external network, including the internet. Physical Air-Gapped Methods for password sharing apply this by ensuring credentials never traverse a digital network during the sharing process. Instead, passwords are recorded on a physical medium—such as a piece of paper, a USB drive, or even a dedicated hardware token—and then physically handed over to the intended recipient.
How it works is straightforward:
- The password is written down or saved onto a physical storage device that is never connected to any network.
- This physical medium is then securely transported and delivered to the authorized individual.
- The recipient accesses the password directly from the physical medium.
This offline process entirely eliminates the possibility of digital interception, malware compromise during transit, or unauthorized remote access, making it a fundamentally safe way to share passwords when the highest level of security is non-negotiable.
Features & Benefits: Why This is a Safe Way to Share Passwords
The unique characteristics of air-gapped methods provide unparalleled security benefits, underscoring why they deserve a place in any comprehensive discussion about secure password sharing:
- Complete Network Isolation: This is the cornerstone. By never touching a network, the password is immune to remote cyber attacks like hacking, phishing, Man-in-the-Middle attacks, and malware designed to steal credentials.
- Physical Possession Required for Access: Access is contingent on possessing the physical item. This gives you direct and tangible control over who can potentially see the password.
- No Digital Footprint or Logs (During Sharing): The act of sharing itself doesn't create digital logs that hackers could exploit. (Note: The system accessed with the password might log activity, but the sharing method itself remains off the digital radar).
- Immune to Remote Cyber Attacks: Reiterating this key benefit, as no digital pathway for the password to travel means no remote vulnerability during the sharing phase.
- Simple Implementation: No complex software or intricate technical configurations are strictly necessary for the basic method (e.g., writing on paper).
- No Dependency on Technology or Internet: This method works regardless of internet connectivity, power outages affecting networks, or the availability of sophisticated technology.
- Immediate Destruction Capability: A piece of paper can be shredded or burned; a USB drive can be physically destroyed, ensuring the password cannot be recovered from that specific medium.
Pros:
Physical air-gapped methods, while not universally applicable for all password-sharing needs, offer compelling advantages when maximum security is the priority:
- Absolute Protection from Remote Hacking: This is their primary strength and the main reason they are considered an exceptionally safe way to share passwords. If it's not online, it can't be hacked remotely.
- No Subscription Costs or Software Needed (for basic forms): Methods like using paper are essentially free. While encrypted USBs have an initial cost, there are no recurring fees for the method itself.
- Complete Control Over the Sharing Process: You physically dictate who receives the password and under what circumstances.
- Cannot Be Intercepted During Digital Transmission: Since there's no digital transmission, this entire risk category is completely nullified.
- Works in Any Environment: Effective from high-tech corporate offices to remote, off-grid locations.
- Easy to Verify Authenticity Through Physical Handoff: You can confirm the recipient's identity in person, significantly reducing impersonation risks common in digital exchanges.
Cons:
However, this method is not without its significant drawbacks, which limit its practicality for many everyday situations:
- Vulnerable to Physical Theft or Loss: If the paper or USB drive is stolen, lost, or misplaced, the password is compromised or rendered inaccessible.
- Not Practical for Remote Teams or Urgent Situations: Physically transporting a password takes time and is inherently difficult over long distances, making it unsuitable for geographically dispersed teams or when immediate access is required.
- No Audit Trail or Access Logging (for the sharing act): It’s hard to digitally track who shared what with whom and when, which can be a compliance issue in some contexts.
- Risk of Physical Interception During Transport: If using a courier or mail service, the package itself could be intercepted, although measures can be taken to mitigate this.
- Difficult to Update or Revoke Access Quickly: Changing a password requires physically retrieving and replacing all shared physical copies, which is cumbersome.
- May Be Lost, Damaged, or Become Illegible: Paper can tear, get wet, or ink can fade. USB drives can be physically damaged or suffer data corruption.
When and Why to Use This Approach
Physical air-gapped methods are not for sharing your streaming service password with a family member across the country. Their utility shines in specific, high-stakes contexts where the integrity of the shared credential is paramount. This is the ultimate safe way to share passwords when:
- Dealing with Extremely Sensitive Credentials: Think root passwords for critical servers, master encryption keys, access codes for weapons systems, or the credentials for a company's primary financial transaction systems.
- Digital Security is Compromised or Untrusted: If there's suspicion of an active network breach or if the available digital communication channels are known to be insecure or heavily monitored.
- Compliance or Policy Mandates It: Certain industries or government entities (as famously popularized by NSA security protocols, military cryptographic units, and high-security banking departments) require air-gapped procedures for the most sensitive data.
- For One-Time Setup of Secure Systems: For instance, sharing initial administrative credentials for a new, isolated secure server before it's configured for more conventional, yet still secure, remote access methods.
- Creating a "Break Glass" Emergency Kit: Storing essential recovery passwords in a physical safe or secure location for disaster recovery scenarios when digital systems might be offline.
In these situations, the benefits of complete isolation from digital threats outweigh the logistical inconveniences. While managing effective group access control often involves sophisticated digital tools, understanding the niche yet critical role of physical methods is crucial for a comprehensive security posture. For more insights into balancing various access control strategies and how physical methods can fit into a broader security framework, you might want to Learn more about Physical Air-Gapped Methods.
Examples of Successful Implementation
The efficacy of physical air-gapped methods is proven by their adoption in environments where security is non-negotiable:
- Military and Defense Organizations: Regularly use sealed, tamper-evident envelopes to transfer classified system access codes or cryptographic keys.
- Financial Institutions: Often employ secure, encrypted USB drives, transported by trusted couriers, for sharing passwords related to critical banking infrastructure.
- Healthcare Facilities: May use locked physical key exchanges or sealed packages for passwords accessing highly sensitive patient record systems, especially for privileged administrative accounts.
- Government Agencies: Government classified information handlers frequently rely on registered mail or dedicated courier services for transferring high-security credentials.
- Industrial Control Systems (ICS) / SCADA: In critical infrastructure like power plants, passwords for truly air-gapped control systems are often managed physically to prevent remote cyber-physical attacks.
Actionable Tips for Secure Implementation
If you determine that a physical air-gapped method is the necessary safe way to share passwords for a particular scenario, implement it with meticulous care:
- Use Tamper-Evident Envelopes or Containers: These provide a visual indication if the package has been opened or interfered with during transit.
- Implement Dual-Control Procedures: Require two authorized individuals to be present for the creation, sealing, transport, or opening of the password-containing medium (the "two-person rule").
- Document the Chain of Custody: Maintain a log of who handled the physical medium, when, and for what purpose.
- Use Encrypted USB Drives: Even if the USB drive is intended for an air-gapped system, encrypting its contents adds a vital layer of security if the drive is lost or stolen during physical transport.
- Destroy or Securely Wipe Physical Media After Use: Once the password has been transferred and is no longer needed on that medium, shred paper documents, physically destroy USB drives (e.g., by crushing), or use specialized software to wipe them securely.
- Verify Recipient Identity In Person: Before handing over a physical password, confirm the recipient's identity, ideally through face-to-face interaction.
- Use Clear, Unambiguous Handwriting: If writing passwords on paper, ensure they are perfectly legible and cannot be misinterpreted (e.g., '1' vs 'l', '0' vs 'O').
- Store Securely: The physical medium should be stored in a locked safe or secure container when not in transit or active use.
While perhaps perceived as archaic by those immersed in cloud-based workflows, such as digital nomads or students, understanding physical air-gapped methods provides invaluable context in the broader landscape of secure information exchange. For tech-savvy individuals, families safeguarding crucial household information, or small businesses protecting core assets, knowing when and how to employ such robust, offline techniques can be a critical component of a multi-layered security strategy. It’s about choosing the right tool for the job, and sometimes the most safe way to share passwords is the one that never touches the internet.
6. QR Code with Encryption
In an era where digital convenience often clashes with security imperatives, finding a safe way to share passwords and other sensitive information is paramount. One increasingly popular and effective method involves leveraging QR (Quick Response) codes, but with a crucial security layer: encryption. This approach transforms a simple password string into a visually encoded format that can be easily shared across various channels, offering a blend of user-friendliness and robust protection. The core idea is that the password or sensitive data is first encrypted using a strong algorithm, and then this encrypted data is embedded into a QR code. The recipient scans this code using a compatible application, which then decrypts the information, typically using a pre-shared secret key or password that was communicated through a separate, secure channel.

The magic of this method lies in its visual encryption encoding. Instead of transmitting plain text passwords, which are inherently vulnerable, the data is scrambled before it even becomes a scannable image. This makes it a significantly more safe way to share passwords, especially for complex credentials that are difficult to type accurately. The process is straightforward: the sender uses an application to input the password and a secret key, generating an encrypted QR code. The recipient uses a corresponding app, enters the same pre-shared secret key, and scans the QR code to reveal the original password on their device.
Key Features and Benefits
Encrypted QR codes come packed with features that cater to both security and convenience:
- Visual Encryption Encoding: The primary security feature. The password is not just hidden in the QR format but is mathematically scrambled, making the raw QR code unintelligible without the decryption key.
- Mobile Device Compatibility: Natively designed for smartphones and tablets, which almost universally have cameras and can run QR scanning apps. This makes it ideal for on-the-go sharing.
- Offline Scanning Capability: Once the QR code is generated and the recipient has the necessary app and decryption key, scanning and decryption can often occur without an active internet connection, enhancing privacy and accessibility.
- Customizable Encryption Algorithms: Advanced implementations allow users or administrators to choose the encryption standard (e.g., AES-256), offering flexibility based on security requirements.
- Error Correction Built into QR Format: QR codes inherently possess error correction capabilities (often using Reed-Solomon codes). This means the code can still be scanned accurately even if it's partially damaged, smudged, or obscured.
- No Typing Required for Complex Passwords: This is a major usability win. It eliminates the risk of typos when dealing with long, complex passwords, which are crucial for strong security but cumbersome to share manually.
- Can Include Additional Metadata: Beyond just the password, some systems allow embedding related information, like usernames, website URLs, or expiry dates, within the encrypted payload.
Pros: The Upsides of Encrypted QR Codes
This method for sharing passwords offers several compelling advantages:
- Easy to Scan and Use on Mobile Devices: The ubiquity of smartphones with cameras makes scanning QR codes an intuitive action for most users.
- Eliminates Typing Errors for Complex Passwords: Directly addresses a common point of failure and frustration in manual password sharing.
- Can Be Transmitted Through Any Visual Medium: QR codes can be displayed on a screen, printed on paper, or even sent as an image file via email or messaging apps (though the channel itself should be considered for overall security).
- Built-in Error Correction Handles Partial Damage: Offers resilience, ensuring the code remains functional even with minor imperfections.
- Quick Generation and Sharing Process: Creating an encrypted QR code is typically a fast process within a dedicated app.
- Works Without Internet Connectivity for Scanning: As mentioned, the decryption can often be local to the device, which is beneficial in environments with limited or untrusted internet access.
Cons: Potential Drawbacks and Considerations
Despite its strengths, there are limitations and risks to be aware of:
- Requires Compatible QR Scanning App with Decryption: Standard camera apps or generic QR scanners won't work. Both sender and receiver need an app that supports the specific encryption/decryption protocol.
- QR Codes Can Be Easily Copied if Not Protected: The QR code image itself can be screenshotted or photographed. The security relies on the strength of the encryption and the secrecy of the decryption key.
- Limited Data Capacity for Very Long Passwords: While QR codes can store a fair amount of data, extremely long encrypted strings might exceed their capacity or result in overly dense, hard-to-scan codes.
- Vulnerable to Shoulder Surfing During Scanning: An onlooker could potentially see the decrypted password on the recipient's screen if care is not taken during the reveal.
- Requires Pre-Shared Decryption Key or Password: The security of the entire system hinges on the secure exchange and management of this decryption key. If the key is compromised, the encrypted password is also at risk.
- Quality Degradation Can Make Codes Unscannable: Poor printing quality, low resolution, or significant damage (beyond error correction limits) can render a QR code unreadable.
Real-World Applications: Encrypted QR Codes in Action
The versatility of encrypted QR codes has led to their adoption in various scenarios:
- Corporate IT Departments: For distributing WiFi passwords to employees or guests. An encrypted QR code can be displayed, and employees use a company-approved app with a pre-configured key to connect.
- Bitcoin Wallet Applications: Used for sharing wallet addresses or even encrypted private key components, ensuring that sensitive financial information is not easily intercepted.
- Password Manager Apps: Some password managers allow users to generate encrypted QR codes to transfer credentials between their own devices or share specific entries with trusted individuals who also use the same manager.
- Event Organizers: For secure access credential distribution. Encrypted QR codes on badges can store attendee information or access rights, verified by scanners with the appropriate decryption key.
Actionable Tips for Secure Implementation
To maximize the security benefits of this safe way to share passwords:
- Use Strong Encryption Algorithms: Opt for robust, industry-standard encryption like AES-256 whenever possible.
- Share Decryption Keys Through Separate Secure Channels: Never send the decryption key alongside the QR code. Use a different, trusted method (e.g., a secure messaging app with end-to-end encryption, in-person communication, or a phone call).
- Generate High-Resolution QR Codes: Ensure clarity and scannability, especially if codes are to be printed or displayed on various screen sizes.
- Add Password Protection to the QR Code Generation Process: If the app supports it, protect the generation of the QR code itself with a password to prevent unauthorized creation.
- Test QR Codes Before Sharing: Always verify that the QR code is scannable and decrypts correctly with the intended key before distributing it.
- Set Expiration Times for Time-Sensitive Password Sharing: If the shared password is for temporary access, use tools or systems that allow the QR code or the underlying credential to expire.
Encrypted QR codes represent a clever convergence of technologies, providing a notably secure and convenient method for password exchange, especially appealing to tech-savvy individuals, families sharing accounts, and small businesses needing collaborative tools. While not a silver bullet, when implemented with an understanding of its mechanics and best practices—particularly the secure management of decryption keys—it stands out as a powerful tool in the arsenal for protecting sensitive credentials. Its adoption by security-conscious developers in fields like cryptocurrency and enterprise mobility further attests to its potential as a truly safe way to share passwords.
Top 6 Password Sharing Methods Comparison
| Strategy | 🔄 Implementation Complexity | 🛠️ Resource Requirements | 📊 Expected Outcomes | 🎯 Ideal Use Cases | ⭐ Key Advantages |
|---|---|---|---|---|---|
| Encrypted Password Managers | Moderate | Medium (software + subscriptions) | Very High (secure centralized vault) | Teams and families needing shared credential management | Military-grade encryption, cross-device sync, audit trails |
| Secure Messaging Apps with Disappearing Messages | Low | Low (free apps) | High (temporary, ephemeral sharing) | Urgent, one-time password sharing between individuals | No permanent trace, strong encryption, quick sharing |
| Encrypted Email with PGP/GPG | High | Low (mostly knowledge and tools) | Very High (end-to-end encrypted email) | Users requiring encrypted, authenticated email communication | Proven cryptography, user-controlled keys, open-source |
| Secure File Sharing Services | Moderate | Medium (cloud subscriptions) | High (encrypted files with audit) | Enterprises sharing sensitive files under compliance | Client-side encryption, granular access controls, scalability |
| Physical Air-Gapped Methods | Low | Low (physical materials only) | Very High (complete isolation) | Highly sensitive passwords needing offline, out-of-band sharing | Immune to remote attacks, full physical control |
| QR Code with Encryption | Low to Moderate | Low (apps and devices) | Medium-High (visual encrypted transfer) | Mobile-friendly sharing of passwords without typing | Easy mobile use, error correction, offline scanning |
Choosing Your Safest Path for Password Sharing
Throughout this article, we've explored a diverse range of methods to securely share sensitive login credentials, from sophisticated encrypted password managers and secure messaging apps with disappearing messages, to PGP-encrypted emails, secure file sharing services, offline physical methods, and even encrypted QR codes. The common thread among all these options is the paramount importance of protecting your digital assets.
The most crucial takeaway is that finding the truly safe way to share passwords for your specific situation isn't about a one-size-fits-all solution. Instead, it involves a careful evaluation of your needs, the sensitivity of the information being shared, your technical comfort, and the context of the share. Whether you're a tech-savvy individual managing personal accounts, a family sharing streaming services, a small business collaborating on projects, or a student seeking affordable subscription access, the right approach will vary. Mastering a safe way to share passwords is essential for protecting your digital identity, safeguarding financial information, and maintaining the privacy of your online activities in 2025 and beyond.
Your actionable next step is to review the methods discussed and determine which best aligns with your requirements. Consider:
- Who are you sharing with? (Trusted individual, team, temporary access)
- What is the sensitivity of the account? (Banking vs. streaming service)
- What is your and the recipient's technical proficiency?
By consciously choosing and implementing a safe way to share passwords, you are taking a significant step towards a more secure digital life. This proactive approach not only protects your immediate interests but also contributes to a safer online environment for everyone. Remember, the goal is to make security a seamless part of your digital interactions, not a cumbersome afterthought.
For those looking to conveniently and securely manage shared subscriptions for services like streaming, gaming, or collaborative software, platforms like AccountShare offer a streamlined solution. AccountShare incorporates secure mechanisms for sharing access within its framework, simplifying the process while prioritizing the safety of your credentials, making it an excellent complement to your broader strategy for finding a safe way to share passwords.
