
Group Access Management: From Chaos to Control in 2024
Share
Why Group Access Management Changes Everything
Switching from managing individual permissions to a group access management strategy is more than an IT update—it's a complete shift in how you protect your organization's most important assets. The old method of assigning access one person at a time might seem simple for a small team, but it quickly spirals into a tangled, unmanageable mess of permissions. This complexity is not just an administrative burden; it's a huge security blind spot.
Think about it: when an employee changes roles, who is responsible for revoking every single permission from their old position? More often than not, nobody is. This leads to permission creep, where users steadily accumulate more access rights than they need for their job. This situation creates a substantial risk from insider threats, whether intentional or accidental.
The Real-World Impact on Security and Compliance
Let's walk through a common scenario. A marketing specialist is promoted to a role in product development. In a traditional setup, an admin would grant them new access to developer tools. However, they might easily forget to remove access to the company's social media schedulers or advertising accounts. Now you have someone with keys to sensitive, customer-facing platforms who no longer has any business being there.
With group access management, this entire problem is solved cleanly. The employee is simply moved from the "Marketing" group to the "Product Dev" group. All their old permissions are revoked, and the new ones are granted automatically. This simple action is what turns stressful compliance audits into routine checks. Instead of painstakingly proving each individual’s access is correct, you just show that your group policies are solid and properly enforced.
This approach is not just a niche trend; it's becoming standard practice. The global Identity and Access Management (IAM) market, which is built on these principles, generated about $14.7 billion in 2022. That figure is expected to jump to $22.2 billion by 2025, showing that businesses are waking up to the need for smarter, scalable security. You can find more details about these trends in recent Identity and Access Management market research.
To better understand the differences, let's compare the old way with the new. The table below breaks down how group-based systems stack up against traditional, individual-based access control.
| Feature | Traditional Access Control | Group Access Management | Business Impact |
|---|---|---|---|
| Assignment | Manual, per-user basis | Role-based, automated | Drastically reduces manual work for IT teams. |
| Updates | Prone to error and oversight | Consistent and immediate | Minimizes security gaps during role changes. |
| Auditing | Complex and time-consuming | Simple and straightforward | Makes compliance audits faster and less painful. |
| Scalability | Poor; becomes chaotic with growth | Excellent; scales with the organization | Supports business growth without security compromises. |
| Security Risk | High risk of "permission creep" | Low risk; permissions are tied to roles | Strengthens security posture against insider threats. |
| Visibility | Fragmented and unclear | Centralized and clear | Provides a clear view of who has access to what. |
This table clearly shows that moving to group access management isn't just about efficiency. It's about building a more secure, compliant, and scalable foundation for your entire organization.
Visualizing Control and Efficiency
A well-designed group access management system offers a clear, high-level overview of who can access what, which greatly simplifies security oversight. This visual approach transforms how you think about permissions.
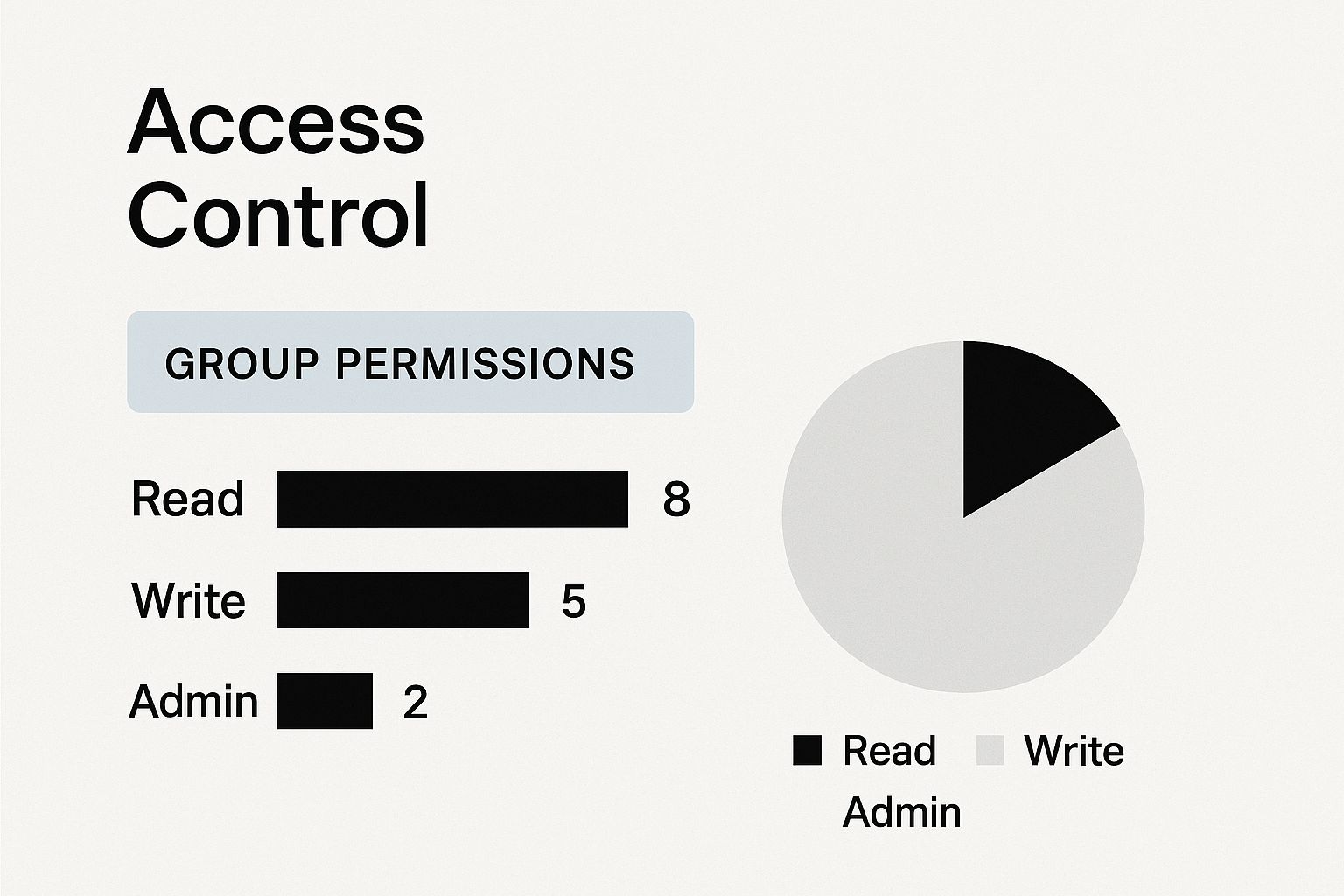
As the infographic illustrates, instead of getting lost tracking thousands of individual connections, administrators can focus on managing a smaller, more logical set of groups. This not only bolsters security but also frees up your IT team from an endless cycle of permission tickets, allowing them to focus on more strategic work. It moves access control from a reactive, chaotic task to a proactive and organized security function.
Mapping Your Access Landscape Before You Build
Jumping straight into configuring access groups without a clear plan is like trying to build a house without a blueprint. The most successful group access management projects start with a detailed assessment of your current environment. This initial groundwork is what separates a streamlined security asset from a chaotic compliance liability.
It all begins with an honest audit to map out who has access to what, right now. You might be surprised by what you find. This isn't just about listing official permissions; it's about uncovering the "shadow access" that builds up over time—temporary permissions that were never revoked or shared accounts with multiple, unknown users. Many organizations discover that their actual access patterns don't match their formal policies. The key is to document everything, creating a full inventory of users, data, and applications. This isn't just busywork; it's the foundation for your entire security structure.
Understanding Your Users and Data
Once you have a baseline, the next move is to categorize what you’ve found. Not all users are the same, and not all data carries the same risk. Start by identifying user archetypes within your organization.
- Standard Users: These are your everyday employees who need access to common, non-sensitive resources like internal wikis or general software.
- Power Users: Think team leads or specialists who require broader access to departmental tools and reports.
- Administrators: This is your technical staff with elevated privileges to manage systems and infrastructure.
- External Collaborators: Contractors, partners, or clients who need temporary, restricted access to specific project files.
At the same time, classify your data based on its sensitivity. For instance, public marketing materials are low-risk, while customer financial records or proprietary source code are highly sensitive. When you map these user archetypes to your data classifications, you get a clear view of the most critical access pathways you need to protect.
Documenting for a Solid Foundation
This process of auditing and classifying paints a clear picture of your access control needs. To see how identity management fits within a larger system, take a look at the diagram below.

This diagram shows that identity management is a central system that interacts with everything from user directories to the specific applications people need. Your audit essentially reverse-engineers this map for your own organization, showing you where the connections are strong and where they are dangerously undefined. This documentation becomes your single source of truth, guiding every decision you make as you design and implement your new group access management rules in a tool like AccountShare. Without it, you are simply guessing.
Designing Groups That Actually Make Sense

After mapping out your access landscape, it's time to build a group access management structure that is both secure and sensible. A common pitfall is creating groups that are either way too broad, like an "All Employees" group, or far too narrow, like "Jane's Project Team." The first approach grants too many permissions, while the second becomes a nightmare to manage. The key is to design groups that mirror how your business actually functions, not just a list of individuals.
A fantastic place to start is with Role-Based Access Control (RBAC). Instead of focusing on what one specific person needs, you define roles within your company—think "Accountant," "Sales Representative," or "System Administrator." Each role gets its own group with a standard set of permissions. When a new accountant starts, you just add them to the "Accountants" group. This method makes onboarding a breeze and automatically applies the principle of least privilege. As we've covered before, effective user permissions management is a huge boost to your security posture.
Structuring for Complexity and Change
Of course, the real world is more complicated than simple job titles. You'll have cross-departmental projects, temporary contractors, and other unique situations. This is where nested groups come in handy. For example, you might have core groups like "Marketing Team" and "Engineering Team." For a joint initiative, you can create a "Project Phoenix" group and add the Marketing and Engineering groups as members. This grants the necessary access for the project without messing with your fundamental role-based setup.
Another area that demands special attention is managing your administrator accounts. This discipline is known as Privileged Access Management (PAM), and it's a critical component of group access. With security threats on the rise, the demand for PAM solutions is exploding. The market was valued at USD 3.65 billion in 2024 and is expected to climb to nearly USD 29.88 billion by 2034. This trend sends a clear message: protecting privileged accounts is non-negotiable for modern businesses. You can get more details from the full privileged access management market forecast. By creating distinct, heavily monitored groups for these high-power accounts, you build a much stronger defense against potential breaches.
Building Automation That Enhances Rather Than Replaces
Let's be honest, trying to manage access permissions manually is a losing battle. As your team expands, what used to be a manageable task quickly becomes a full-time job, a major bottleneck, and a huge security risk. But diving into automation without a solid plan can backfire, creating more problems than it solves. The key is to find a smart balance, using automation to empower your team while maintaining tight security and human oversight where it counts.
This is especially true for common employee lifecycle events. When someone joins the company, automation can grant them the access they need based on their role from the moment they start. No more waiting around for IT tickets to be resolved. On the other side, when an employee leaves, their access must be revoked instantly. This is a critical security step that often gets missed in manual processes. In fact, a recent study highlighted that 50% of ex-employees could still access company accounts after their departure. Automation transforms this high-risk task into a reliable, immediate action.
Handling Everyday Scenarios
Where automation really proves its worth is in managing the day-to-day requests that typically flood the IT helpdesk. By setting up intelligent approval workflows, you can keep work moving without sacrificing control.
To see the real-world impact, let's compare how automation handles common situations versus a manual approach. The table below shows just how much time you can save and how much risk you can reduce.
| Scenario | Manual Process Time | Automated Process Time | Risk Reduction |
|---|---|---|---|
| New Hire Onboarding | 1-3 business days | 5 minutes | Low |
| Role Change | 2-4 hours | 2 minutes | Medium |
| Project Access Request | 1-2 business days | 10-15 minutes (with approval) | Low |
| Employee Departure | 24-48 hours (or missed) | Instantaneous | High |
As you can see, the time savings are impressive, but the biggest win is the drastic reduction in security risks, particularly during offboarding. For a deeper dive into this, our guide on effective group access control has some excellent pointers.
However, automation isn't a silver bullet for every single request. Some situations, like granting access to highly sensitive systems, still require a human touch. A practical approach is to automate about 90% of routine requests while flagging the remaining 10%—the high-privilege, unusual ones—for manual review. This ensures that a person always makes the final call on the most critical access decisions.
Monitoring Access Without Drowning in Alerts
You’ve set up your groups and automated the provisioning—that's a major win. But the real work of group access management is just beginning. The long-term challenge is keeping everything as clean and secure as the day you launched it. Proper monitoring is what separates a quickly contained issue from a front-page data breach. The idea isn't to create a firehose of alerts but to build a system that gives you real intelligence, not just noise that your team will eventually ignore.
The focus on strong access systems is only getting more intense. The Access Management market is on track to become a USD 31.25 billion industry by 2030, which shows just how seriously organizations are taking digital security. This isn't just a niche concern anymore; it's a fundamental part of business. You can dive deeper into this trend with the latest worldwide access management market forecast.
Building a Dashboard That Tells a Story
The first thing you need is a monitoring dashboard that gives you a clear, immediate picture of your access landscape. Forget about scrolling through endless log files. Your goal is to visualize the key indicators that signal trouble.
- Failed Login Attempts: A few typos happen, but a sudden surge from one user or location is a classic sign of a brute-force attack.
- Privileged Account Activity: Every action taken by an admin account should be logged. Your dashboard needs to spotlight any unusual activity, like someone logging in at 3 AM or accessing systems unrelated to their job.
- Group Membership Changes: Keep a close eye on who gets added or removed from important groups. This is your best bet for catching an unauthorized privilege escalation right away.
- Access to Sensitive Data: You need to know who is touching your most critical information. If someone from marketing suddenly starts accessing R&D files, that’s a red flag that requires immediate attention.
The Power of Regular Access Reviews
Beyond what you see on a dashboard, periodic access reviews are your secret weapon against "permission creep." This is where you schedule time for department heads or data owners to look at who has access to their resources and simply ask, "Does this person still need this?" Think of it less like a formal audit and more like a collaborative security check-in.
This simple process is incredibly effective at trimming unneeded permissions and shrinking your potential attack surface. It's a foundational security measure we cover in our guide on the top access control best practices. By blending a smart, visual dashboard with these routine reviews, you move from a reactive stance to a proactive security posture.
Solving Problems Before They Become Disasters
Even the most carefully planned group access management system will eventually have a bad day. The real measure of your setup isn't whether problems happen, but how fast you can find and fix them before they stall work or, worse, create a security gap. Being prepared with a troubleshooting plan is much better than scrambling during a crisis.
Let's walk through a common scenario: your marketing team suddenly loses access to a shared drive they rely on daily. Before panic sets in, consider the most likely culprit: a permission conflict. This often happens when a user belongs to multiple groups, and one of them—perhaps a nested group they were added to indirectly—is accidentally denying access. The trick is to trace the user's complete membership path, not just their main role. Tools that can visualize group inheritance are invaluable here, as they can quickly pinpoint where the conflicting rule is hiding.
Diagnostic and Prevention Strategies
Making your group access management system resilient is about more than just reactive fixes. It involves proactive steps to prevent issues from cropping up in the first place. This means combining smart diagnostics with clear communication.
- Isolate the Issue: When an access problem hits, your first question should be, "Is this affecting just one person, the whole group, or everyone?" This simple step helps you instantly narrow down the cause. A single user issue points to their account, while a group-wide problem suggests a policy error.
- Communicate Clearly: Keep your users informed. A quick message like, "We've found an access issue with the 'Sales Team' group and are actively working on it" can prevent a flood of support tickets and manage everyone's expectations.
- Review Group Membership Regularly: Set up quarterly reviews to make sure group memberships are still accurate. People switch roles, and projects come to an end. These checks are your best defense against permission creep, where users slowly accumulate access they no longer need.
Handling Edge Cases and Building Resilience
Sometimes, the problem isn't a straightforward conflict but a unique situation. For example, you might need to give a temporary contractor access to several restricted project folders. Instead of adding them to multiple core teams—a move that could grant them too much access—create a dynamic access group. You can tie this group to a specific project timeline, so their access automatically ends on a set date. This approach neatly closes the security loop without manual follow-up.
True resilience also means having a solid backup and recovery plan for your access control system itself. You should always know how to restore your group configurations to a previous, stable state. This ensures that even in a worst-case scenario, you can get things back online quickly and securely while you sort out the root cause.
Your Roadmap to Group Access Management Success
Putting a solid group access management strategy into motion requires a clear plan that actually fits how your organization works. Whether you're starting from scratch, tweaking what you already have, or cleaning up after a security incident, the journey begins with an honest look at your current state and some practical next steps. Let's skip the fancy slide decks; real success is built on a few core ideas.
The most important thing is to make sure your groups mirror how your business truly operates. This means going beyond simple job titles. Think about the access people need for their daily tasks, for temporary projects, and for when different departments need to work together.
Building a Realistic Timeline
Rolling out a new access system isn't just a technical task—it's a change in how your organization functions. Your timeline needs to reflect this human element. Don't expect everyone to jump on board immediately. You'll likely face some resistance and run into complexities, so be sure to schedule time for training and gathering feedback.
A practical way to manage the rollout is to break it into phases:
- Phase 1: Critical Systems First. Start by securing your most sensitive data and applications. This gives you the biggest security win right away and helps show the value of the project to any doubtful stakeholders.
- Phase 2: Departmental Rollout. Go one department at a time. This lets you learn and perfect your process with a smaller, more manageable group before you expand it to the entire company.
- Phase 3: Fine-Tuning and Automation. After the main structure is in place, you can focus on automating tasks like setting up and removing access, and establishing ongoing monitoring.
Tracking Progress and Celebrating Wins
To keep things moving forward, you need to track your progress with clear metrics. Keep an eye on the number of help desk tickets for access requests—hopefully, it's going down! Or, measure how long it takes to get a new employee fully set up. These numbers give you real proof that your efforts are paying off.
You should also be on the lookout for red flags. If you see a sudden increase in one-off permission overrides or hear complaints that the new system is too restrictive, it’s a sign that you might need to rethink your group structures. And don't forget to celebrate your successes along the way. Recognizing a smooth departmental rollout or a perfect access audit keeps your team motivated and invested in the long-term security of your company.
Ready to build a smarter, more secure access system? Discover how AccountShare can help you manage shared premium services with ease and control.
